Here’s How You Can Change Your Twitch Username [2022]
Changing the username changes the URL of the Twitch channel.
Technology’s ultimate purpose is to make things easier for us. In this section, we try to bolster that goal with our in-depth yet simple how-to articles. These guides are one of the top-visited pages of Fossbytes. These pieces revolve around simple and useful tips to improve the productivity of your computers, phones, and other devices. We also try to solve hot searched problems and queries requested by the users in this section.
![Here's How You Can Change Your Twitch Username [2022]](https://fossbytes.com/wp-content/uploads/2022/02/Heres-How-You-Can-Change-Your-Twitch-Username-2022-768x432.png)
Changing the username changes the URL of the Twitch channel.

Clear Cache on iPhone & iPad

Host a meeting from wherever you are, on whichever device you want.

disconnect social media and delete contacts
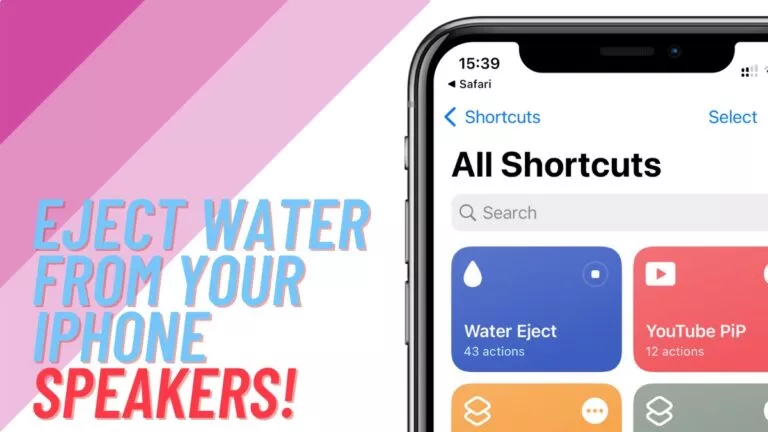
Here’s how to easily get the water out of your iPhone’s speakers.

Get rid of annoying messages and spam.

Here’s how you can access these particular websites.

Scheduling Zoom sessions is as easy as they come.

Hosting on Twitch is a fairly easy task.
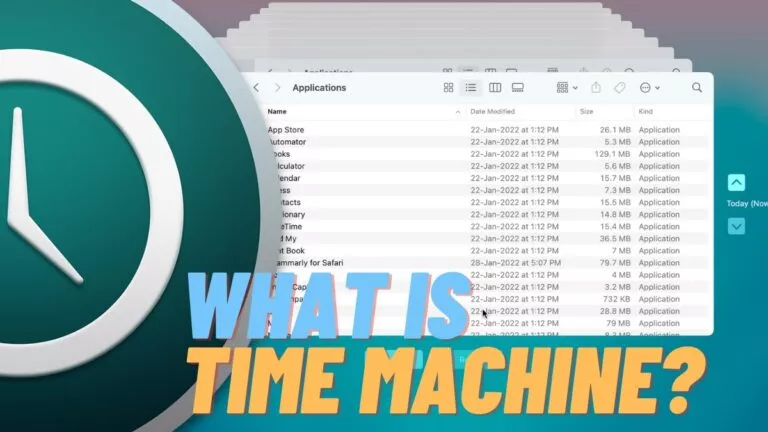
It’s no less than a real time machine!