Why Solana Is One of the Fastest Blockchains in the World
When people talk about blockchain speed, they usually mean one of two things: how quickly transactions…

When people talk about blockchain speed, they usually mean one of two things: how quickly transactions…

As organizations accelerate their migration to cloud-native architectures, Kubernetes has become the de facto orchestration platform…

After ChatGPT and other large language models were released, people online started raising concerns about data…

It’s no secret that Jujutsu Infinite is a super fun Roblox game, where you get to…

Ghoul Re is an exciting Roblox game based on the dark universe of ghouls and humans,…

Inspired by the super-popular anime and manga series Bleach, Type Soul is a Roblox game where…
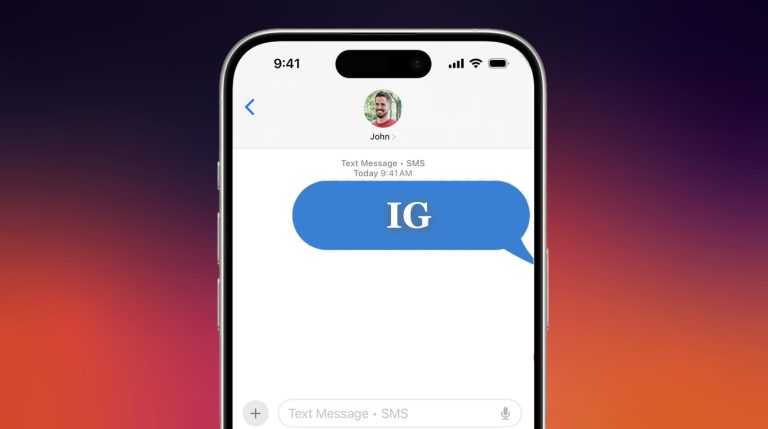
Internet slang changes fast, and sometimes you’ll see something in a message or a post that…
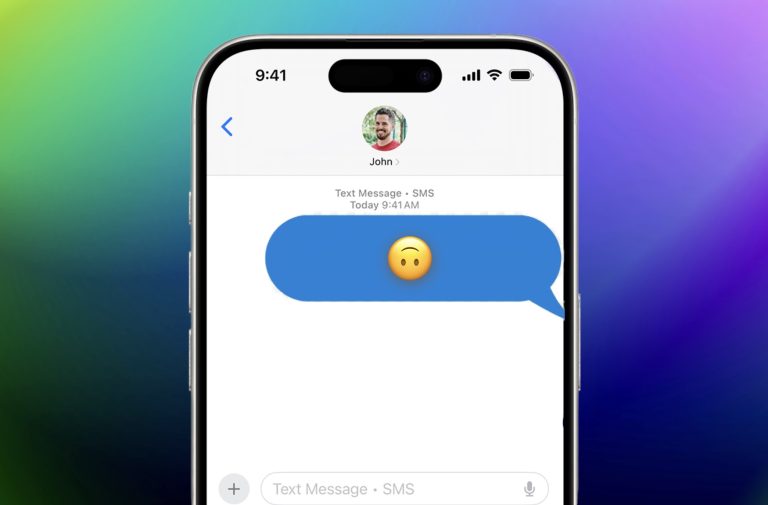
Emojis are a crucial tool to convey mood and context in our communication. When texting a…

Privacy is no longer just a buzzword—it’s the basis of trust online. As surveillance grows and…
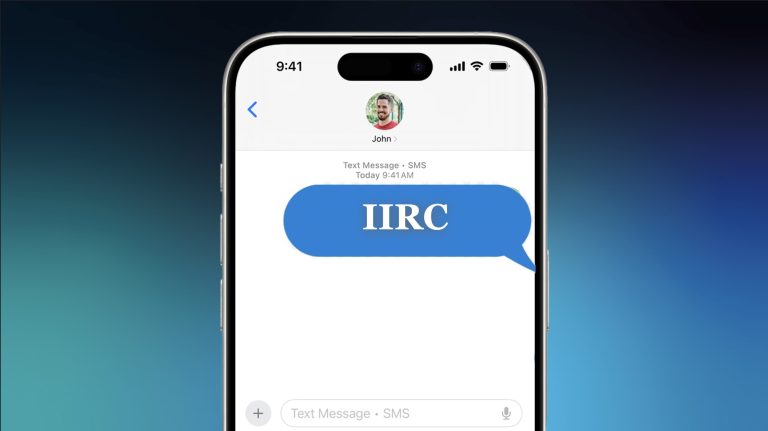
Understanding the new slang and abbreviations is the secret to communicating effectively in the ever-evolving social…