Windows Malware Steals 26 Million Passwords: How To Check If I’m Affected?

After the Dominos India data theft, data from a 1.2TB database containing browser autofill data, cookies information, usernames and passwords, and payment information has been taken away by unidentified malware, according to researchers from NordLocker.
The stolen data contained over 2 billion browser cookies, 1.1 million email addresses, 6.6 million files, and over 26 million login credentials. These files also included people’s passwords stored in a text file created using Notepad and 650000 Word and PDF files, and over 1 million images.
According to Ars Technica, the malware also took a screenshot and took a picture using the webcam after infecting the computers. This happened between 2018 and 2020, and over 3 million PCs were affected.
What Will Happen To The Data?
In a conversation with Ars Technica, Alon Gal, co-founder and CTO of Hudson Rock, said, “The attacker will likely then try to steal cryptocurrencies, and once he is done with the information, he will sell to groups whose expertise is ransomware, data breaches, and corporate espionage.”
Security researchers at NordLocker said, “The truth is, anyone can get their hands on custom malware. It’s cheap, customizable, and can be found all over the web. Dark web ads for these viruses uncover even more truth about this market. For instance, anyone can get their own custom malware and even learn how to use the stolen data for as little as $100.”
How To Check If Your Data Was Leaked?
The details of this nameless Malware have been added to Have I Been Pwned website. You can check if your data was leaked by searching for your email address or phone number in the website’s search bar.
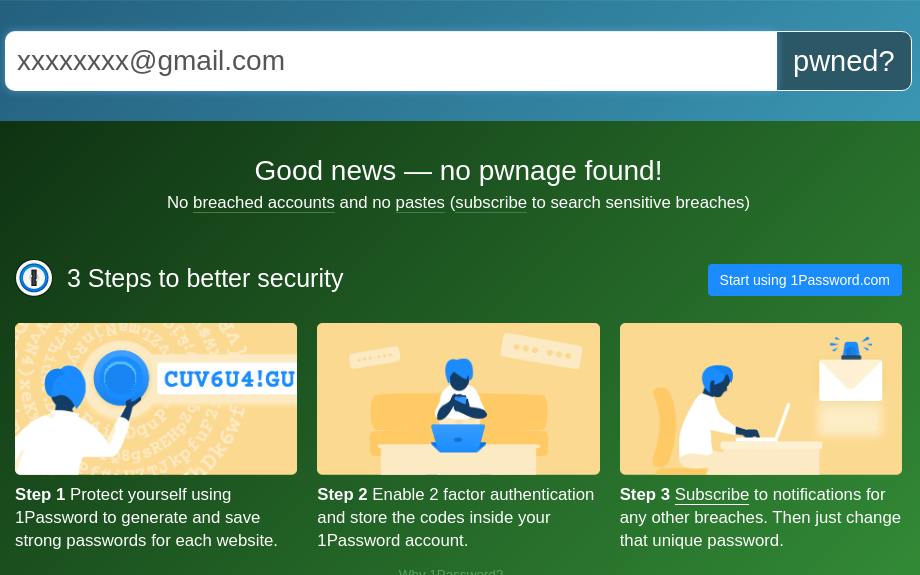
After entering your email address click on the pwned? button. If your data was leaked in any major data breaches, you’ll see something like this.
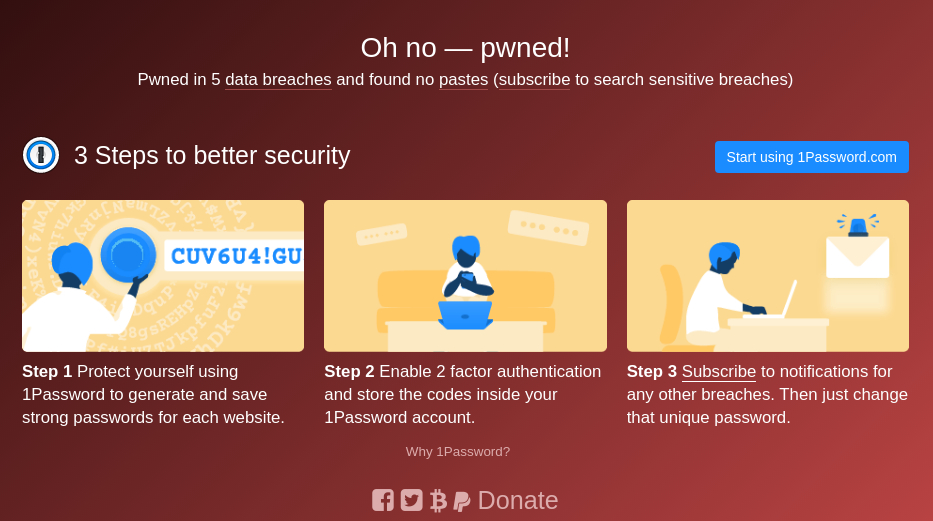
By scrolling down, you’ll be able to see the websites or apps on which your data was compromised.

What are your views on data privacy? Do you think it’s slipping from our hands, and we should invest more in privacy than making complex systems even more complex? Let us know in the comments section below.