Why Solana Is One of the Fastest Blockchains in the World
When people talk about blockchain speed, they usually mean one of two things: how quickly transactions…

When people talk about blockchain speed, they usually mean one of two things: how quickly transactions…
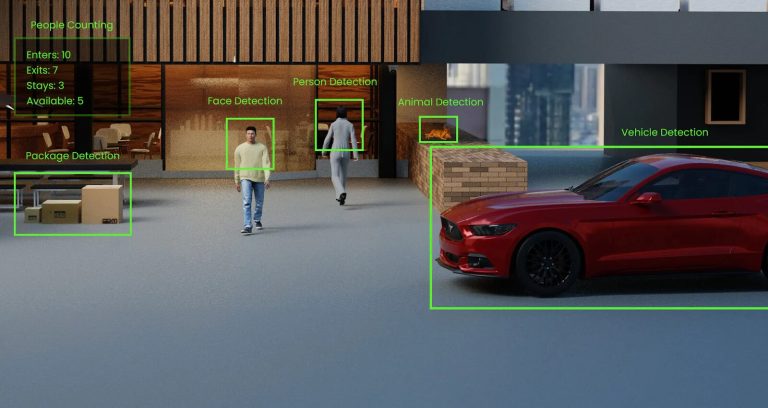
There is a new wave of organized crime sweeping across cities, where criminals increasingly target USPS…

During the COVID-19 pandemic, when everyone was home, remote work was the only way for people…

Teaching kids how to stay safe online is essential in today’s digital world. Fun games can…

According to a study undertaken in 2023, around 71% of US adults are now worried about…

The instances of websites getting blocked are rising each year due to numerous factors. In many…

In today’s digital age, understanding the operations of the world’s most powerful ransomware groups is crucial….
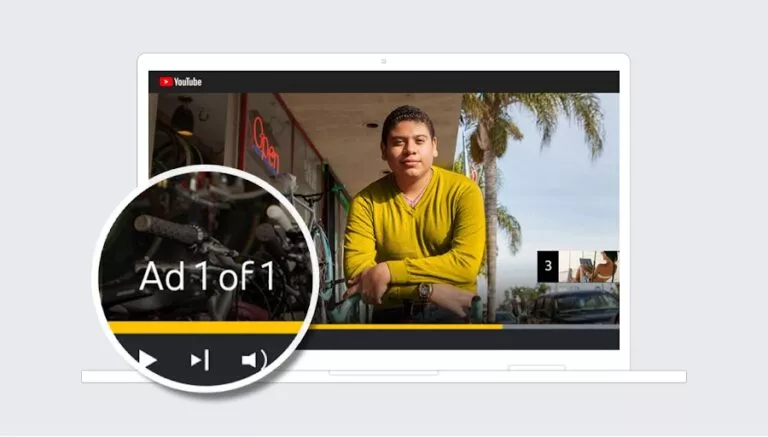
When YouTube first debuted ads, they weren’t intrusive and provided creators a way to earn money….

The internet offers a platform for connection, communication, and collaboration, but it also opens the door…

In this day and age, where threat actors are always on the lookout to gain unauthorized…