HORNET: Tor-like Anonymity Network With Superfast Speeds

 The Deep Web is a place that is hidden from the ordinary world because the browsers used to access the Deep Web, continuously encrypt user data. Due to this constant data encryption, the browsing speeds are slow. Our beloved Tor network has more than 2 million daily users that slow down its performance. To counter this speed issue, five researchers have developed a new Tor-style anonymity network called HORNET: High-Speed Onion Routing at Network Layer.
The Deep Web is a place that is hidden from the ordinary world because the browsers used to access the Deep Web, continuously encrypt user data. Due to this constant data encryption, the browsing speeds are slow. Our beloved Tor network has more than 2 million daily users that slow down its performance. To counter this speed issue, five researchers have developed a new Tor-style anonymity network called HORNET: High-Speed Onion Routing at Network Layer.
This paper “Hornet: High-Speed Onion Routing at Network Layer” was written by researchers Chen Chen of Carnegie Mellon University, along with David Barrera, Enrico Asoni, and Adrian Perrig of Zurich’s Federal Institute of Technology, and George Danezis from University College of London. Here’s the research paper.
To achieve speeds higher than Tor, HORNET doesn’t encrypt data as often- instead it encrypts just the personal stuff. In Tor, anonymity comes at the price of speed. To provide anonymity, Tor takes data and passes it through series of computers before the final destination. Each time, it passes from one computer to the other, the encryption exists and IP addresses change. Thus, it forms a time-taking multilayer network (hence “The Onion Router”).
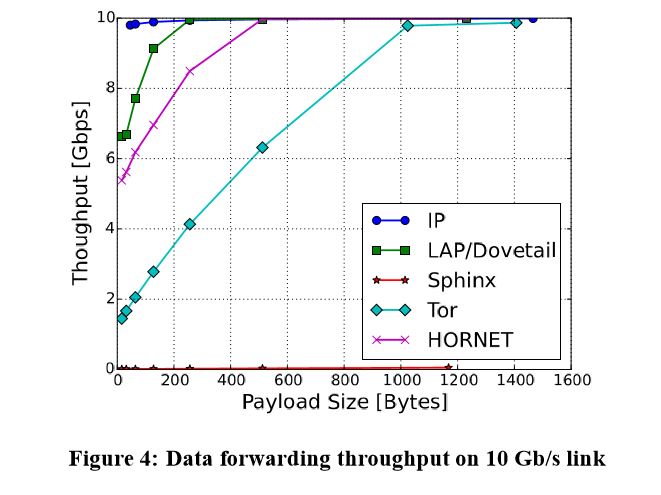 HORNET nodes process the anonymous traffic at more than 93Gb/s speed.
HORNET nodes process the anonymous traffic at more than 93Gb/s speed.
The basic architecture of Tor and HORNET is same(onion routing). HORNET creates an encryption key set along with the routing info (connection state) on your system. Thus, the intermediate nodes don’t need to build this information each time, as these keys and connection state info is carried within packet headers (anonymous header or AHDR).
Also read: Best Alternatives to Tor Browser to Browse Anonymously
According to the research paper, it makes the whole system more secure as the other intermediate computers don’t waste time playing with the sender’s and receiver’s packets. Thus, the whole process becomes more fast and secure.
It is worth mentioning that HORNET is not yet tested at a large scale, it’s just these 5 researchers. Thus, extensive peer review is needed to adopt systems like HORNET.
Did you like this story? Tell us your views about HORNET in comments below.






