Fake Kodi Repos ‘Hijack’ Original GitHub Accounts To Push Updates

Developers of Kodi add-ons usually host their tools on GitHub. While the popular code repository platform is perfect for development, it has one loophole which has been exploited for quite some time.
When users sign up on GitHub, they’re allocated a unique URL. However, when developers delete their account, their namespace can be used by anyone leading to the generation of the same URL which allows fake Kodi-addons to pull updates that weren’t provided by the original developer.
It’s not the first occurrence of this issue, as famous Kodi add-on developer MetalKettle highlighted it years ago. After he deleted his GitHub repo, a third-party signed up on the platform with the same username to obtain the same URL.
This means that the third-party can push updates to users who were using MetalKettle add-ons in their Kodi setup. It is quite dangerous because a previously-trusted URL could easily be replaced by a potentially malicious third-party.
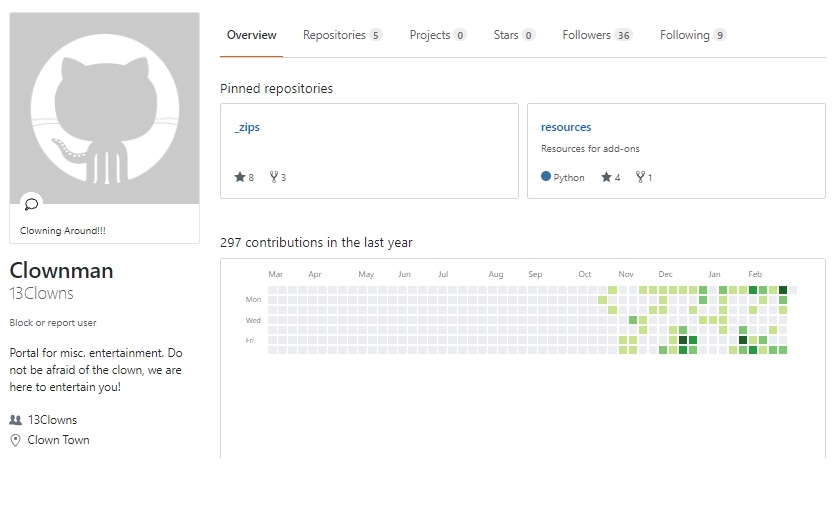
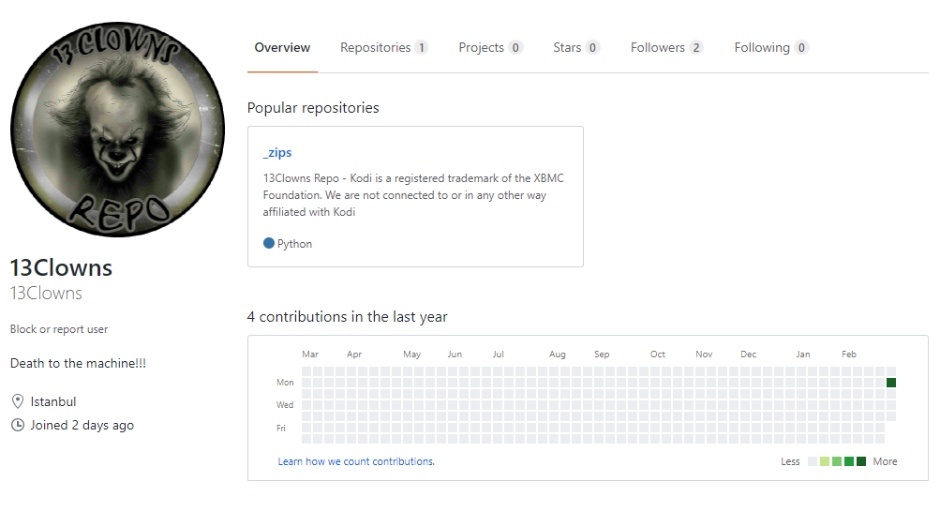
Recently, another such ‘hijacking’ of accounts took place when the popular ’13Clowns’ repo was deleted by its developer. The namespace was quickly taken over by a third party with the same name and, of course, the same URL.
The following images show the difference between the original repo (first) and imposter repo (second).
So, the imposter ’13Clowns’ began sending updates to former users of the original repo. The new updates included a fork of the Exodus add-on along with tools from TVAddons — a controversial Canada-based Kodi add-on indexing site.
In response, GitHub says that its namespace retirement policy can deal with this type of abuse by taking steps against such repos which violate and exploit this loophole.
Meanwhile, developers can protect their repos by not deleting their GitHub accounts and remain in charge of their own repos.
Also Read: How To Fix Kodi Not Working Issues? 5 Troubleshooting Tips