Flaw In SSDs Allows Hackers To Access Encrypted Data Without Password

A researcher from Radboud University has uncovered a flaw in some Solid State Drives (SSDs) that is allowing hackers to bypass disk encryption and access the data without requiring the encryption password.
The vulnerability has affected only those SSD models supporting hardware-based encryption which uses local built-in chips for carrying out disk encryption operations. These chips are separate from the main CPU.
Drives that use hardware-based encryption are commonly known as Self-Encrypting Drives (SEDs) after software-based encryption was deemed susceptible to the attacks. It allowed the hackers to grab hold of the encryption password from the computer’s RAM.
Researchers named Carlo Meijer, and Bernard Van Gastel from Radboud researchers published an academic paper revealing the flaw exploits “ATA Security” and “TCG Opal” — the two specifications used for implementing hardware-based encryption in SEDs.
Users could set a custom password for accessing the encrypted data. However, a master password set by the SED vendor could be used by the hackers to gain access to the user’s password leading. The master password is available in the SEDs manual and can be used by anyone.
To evade this vulnerability, one needs to change the master password or configure the master password capability to maximum, thus disabling it altogether.
Master password and flawed implementation of the standards are the culprits behind this vulnerability.
The security researchers said, “Absence of this [cryptographically linking] property is catastrophic. Indeed, the protection of the user data then no longer depends on secrets. All the information required to recover the user data is stored on the drive itself and can be retrieved.”
The vendors of the SEDs that were tested while publishing the research papers — Samsung and Crucial (Micron) have released firmware updates to eliminate the flaw.
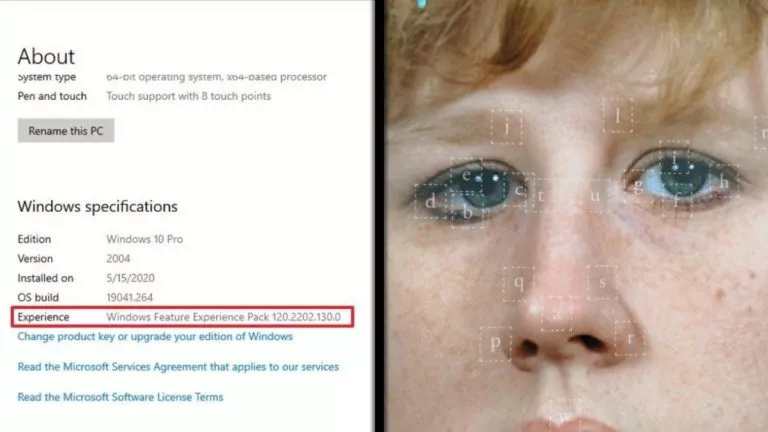
However, the issue runs deeper. Windows users are more risk-prone as the Windows BitLocker, a software-level full disk encryption system of Windows OS does not encrypt the users’ data at the software level upon detecting a device capable of hardware-based encryption.
The researchers have recommended the SED users to use software-level full disk encryption systems such as VeraCrypt to protect their data.
Furthermore, the SED vendors have also asked the TCG working group to “publish a reference implementation of Opal to aid developers,” and to make the flawed implementation public so that more security researchers can find the vulnerabilities lying in the specifications.