Dharma Ransomware Installs Antivirus On PC Only To Encrypt Files Later

Dharma Ransomware is out on the loose and is evolving by the minute. The latest report from Trend Micro has spotted instances of Dharma Ransomware encrypting files by distracting users with an antivirus installation.
Dharma ransomware is a version of Crysis, which is another dangerous malware. Dharma encrypts user files using Asymmetric Cryptography. It is a method in which bits present inside the file are encrypted. In the Asymmetric Cryptography process, the output of encryption is text, even if the input is non-text.
Dharma Ransomware Uses Real Anti-Virus For Malware Attack
In the latest attempt to cause havoc online, Dharma Ransomware is spamming users with an e-mail titled ‘MSC-ALERT-IMPORTANT!’. The e-mail contains a system corrupt warning which prompts the user to click and download an older version of ESET Antivirus.
The e-mail prompts the user to download and verify their anti-virus using an attached password. The download file is a self-extracting archive called Defender.exe. It contains two files and the antivirus software installer.
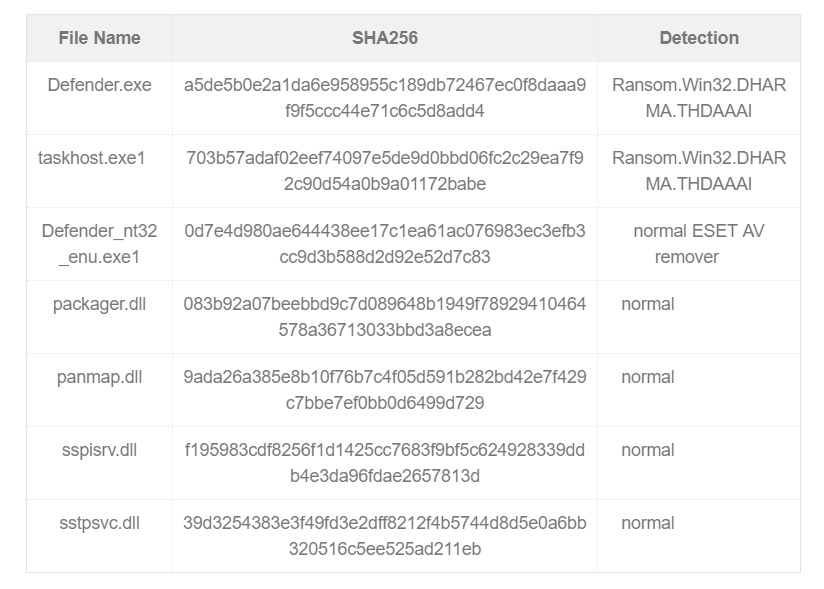
The two malicious files are taskhost.exe and Defender_nt32_enu.exe. The first file activates the Dharma Ransomware itself as RANSOM.WIN32.DHARMA.THDAAAI.
Ransomware does its best job to keep users busy with anti-virus installations as it encrypts files in the background. The ESET antivirus installer is absolutely real and works just fine.
Furthermore, the installation process of ESET antivirus is in no way related to Dharma Ransomware. It is to be noted that the encryption of files due to ransomware attacks and anti-virus installations occur separately.
This is how Dharma Ransomware works:
- User receives MSC-ALERT-IMPORTANT spam e-mail
- The email prompts the user to click and download the anti-virus that has attached Dharma ransomware.
- User opens a password protected archive using the attached password in the e-mail
- Installation window of ESET antivirus appears to activate Defender.exe
- Defender.exe drops Taskhost.exe and Defender_nt32_enu.exe
- Taskhost.exe is Dharma ransomware posing as RANSOM.WIN32.DHARMA.THDAAAI
- It encrypts the file while the antivirus installation continues in the background
SHA256 Codes of Dharma Ransomware Files
Current State of Ransomware Attacks
Over the past few months, we have observed the changing face of ransomware attacks. The hackers have changed their tactics and are now heavily camouflaging their ransomware as useful tools to deceive users.
For instance, ransomware called VxCrypt improves the performance of a user’s PC while encrypting its files. Some hackers link malware in torrent files of popular TV shows like Game of Thrones.
Another ransomware called Robinhood ransomware encrypts your files with a message. It assures users that their data will be deleted once they pay the ransom.
Even though Ransomware is changing, its fundamental steps remain the same — tricking users into downloading malicious files.
How To Avoid It
Users can protect themselves by following the golden steps of regularly backing up their files offline, limiting administrative access and keeping their anti-virus updated. However, most users can start by changing their password to a strong one because another ransomware called Xwo is out there to get you.
Ransomware attacks are also causing their ill-effects in the real world — from encrypting hospital documents to shutting down industrial plants and even the entire city government. All of us need to take important steps before someone gets hurt for real.
Also Read: ‘Sodinokibi’ Is A New Ransomware That Exploits Oracle Zero Day Flaw