BitTorrent Client Transmission Infected With World’s First Mac Ransomware KeRanger — How To Protect Yourself
 Short Bytes: KeRanger — the world’s first Mac ransomware — has arrived to give you nightmares. Spread via BiTorrent client Transmission, the malware encrypts your computer files and demands a Bitcoin payment to decrypt it. The researchers mention that the malware appears to be under active development and it seems that it also attempts to encrypt Time Machine backup files to forbid the victims from recovering their back-up.
Short Bytes: KeRanger — the world’s first Mac ransomware — has arrived to give you nightmares. Spread via BiTorrent client Transmission, the malware encrypts your computer files and demands a Bitcoin payment to decrypt it. The researchers mention that the malware appears to be under active development and it seems that it also attempts to encrypt Time Machine backup files to forbid the victims from recovering their back-up.
On the website, Transmissionbt.com, the users running Transmission client version 2.90 are asked to immediately upgrade their application and run the latest version 2.92. The website reads that it’s possible that users may have downloaded a malware-infected file. Uncovered by the researchers with Palo Alto Networks Inc., the KeRanger malware is the first functioning ransomware attacking Apple’s Mac devices.
It’s a known fact that the cyber threat of ransomware has risen manifold over the past years. While these were known to typically target the users of Microsoft’s Windows operating systems, the new malware encrypts your computer and demands a Bitcoin payment to decrypt it.
After targeting your Mac, the malware begins encrypting certain types of document and data files. After the process is completed, KeRanger demands that the victim pays one bitcoin ($400) to a specific address to retrieve their files. The researchers mention that the malware appears to be under active development and it seems that it also attempts to encrypt Time Machine backup files to forbid the victims from recovering their back-up.
If we dig deeper, the two KeRanger infected Transmission installers are signed with a legitimate Apple-issued certificate but its developer ID is different from the previous versions. The ransomware-infected file also includes an extra file named General.rtf whose icon looks like a normal RTF file but it’s a Mach-O format executable file. “As soon as a user clicks on an infected app, their bundle executable copies this RTF file to ~/Library/kernel_service and executes this “kernel_service” before any user interface appearing,” researchers write.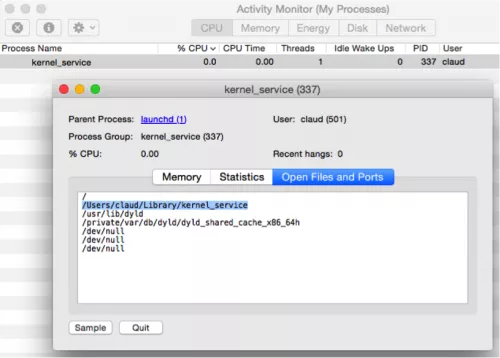
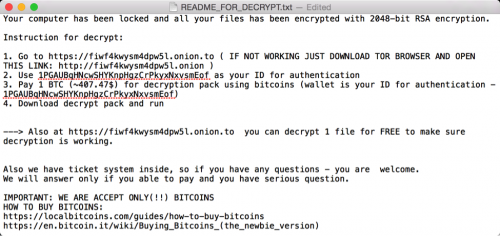
The General.RTF file collects infected Mac’s device information and uploads it to its C2 servers that are accessible over .onion (TOR) domains. The rest part of the functioning includes downloading a text file from C2 server that asks victims to pay the money at the address of “1PGAUBqHNcwSHYKnpHgzCrPkyxNxvsmEof”.
Here’s a screenshot:
How to protect yourself against KeRanger — the world’s first Mac ransomware?
- Using your Mac’s Finder or Terminal, look for /Applications/Transmission.app/Contents/Resources/ General.rtf or /Volumes/Transmission/Transmission.app/Contents/Resources/ General.rtf.
- Open the preinstalled Activity Monitor in OS X and check if a process named “kernel_service” is running. If so, choose Open Files and Ports and look for a file /Users/<username>/Library/kernel_service. This is KeRanger’s main process and you are suggested to terminated it using Force Quit option.
- After the above steps, users are also advised to check if these files are existing in ~/Library directory: .kernel_pid, .kernel_time, .kernel_complete or kernel_service. If you locate these, delete them.
Meanwhile, Apple has updated the XProtect signatures and you’ll be warned if you open a known infected version of Transmission. You are advised to follow Apple’s instructions to keep yourself safe.