What Is A Web App Attack, How Does It Work — 5 Stages Of A Web App Attack

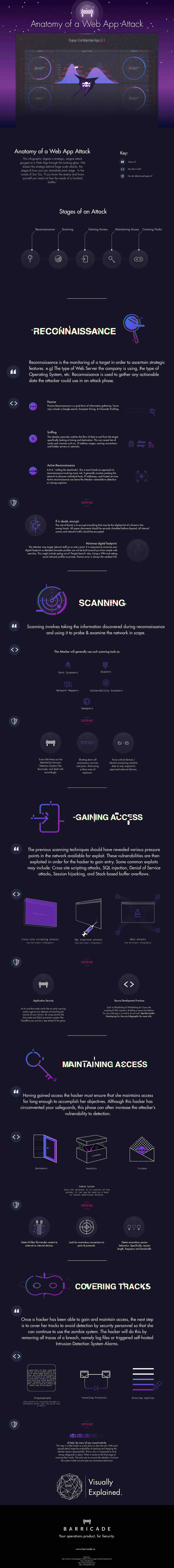
 Short Bytes: A Web App Attack is one of the biggest threats faced by websites and online businesses. In this article, we are going to tell you about 5 stages of a Web App Attack — Reconnaissance, Scanning, Gaining Access, Maintaining Access, and Covering Tracks — and how this attack works.
Short Bytes: A Web App Attack is one of the biggest threats faced by websites and online businesses. In this article, we are going to tell you about 5 stages of a Web App Attack — Reconnaissance, Scanning, Gaining Access, Maintaining Access, and Covering Tracks — and how this attack works.
As the application development is moving more and more onto the web, the Web is home to everything we need. 2015 also saw an increase in Web App Attacks that are carried out using a well-planned plan-of-action. The attack usually targets the web server used by the target company. In spite of network defenses like intrusion penetration systems and firewalls, the Web application could be attacked by an outsider in multiple ways.
What Is A Web App Attack, How Does It Work
In this article, we are going to explain you the five stages of a Web App Attack from a hacker’s perspective. The each stage will be explained into three parts — What is it? How does it work? How do I defend myself against it?
The five stages that will be explained ahead are: Reconnaissance, Scanning, Gaining Access, Maintaining Access, and Covering Tracks.
Let’s take a look at this useful infographic by Barricade, an Early Warning System against Hackers.
Anatomy of a Web App Attack – Visually Explained
Did you find this Web App Attack infographic helpful? Do tell your views in the comments below.
Want To Be Anonymous While Surfing? Why Not A VPN Service?