This Android Malware Attacks Your Wi-Fi Router And Hijacks Web Traffic
Short Bytes: A dangerous Android malware named Trojan.AndroidOS.Switcher has been discovered by the security researchers at Kaspersky Lab. The malware, disguised as two different mobile apps, tries to brute force the password of Wi-Fi routers and control the entire network. Surprisingly, the malicious settings even manage to survive a router reboot. Researchers have shared few rogue DNS servers that users need to check.
The malware targeting the Android operating system aren’t new but we keep seeing different varieties from time to time. One such new Android malware, dubbed Trojan.AndroidOS.Switcher, has been discovered by the researchers at the Kaspersky Lab.The working of this malware makes it pretty unique. Instead of attacking the user, Switcher targets Wi-Fi network of the connected user (or the Wi-Fi router of the network).
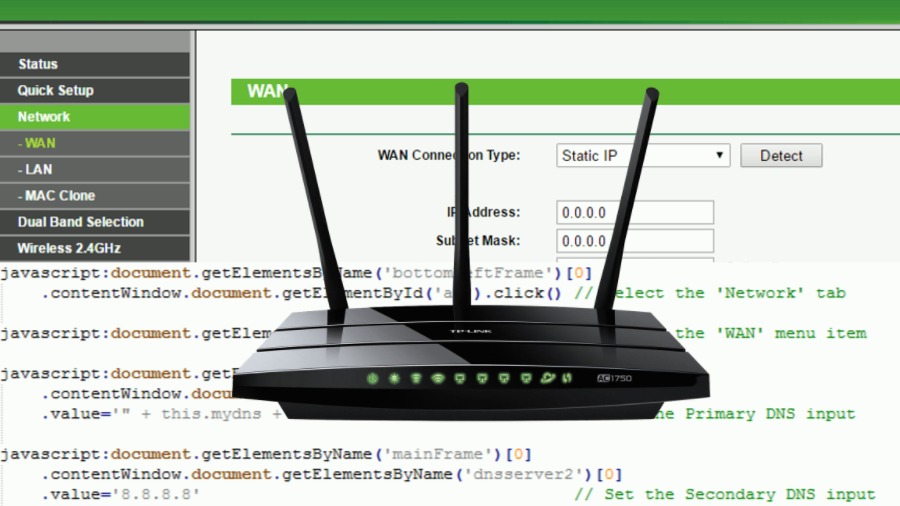
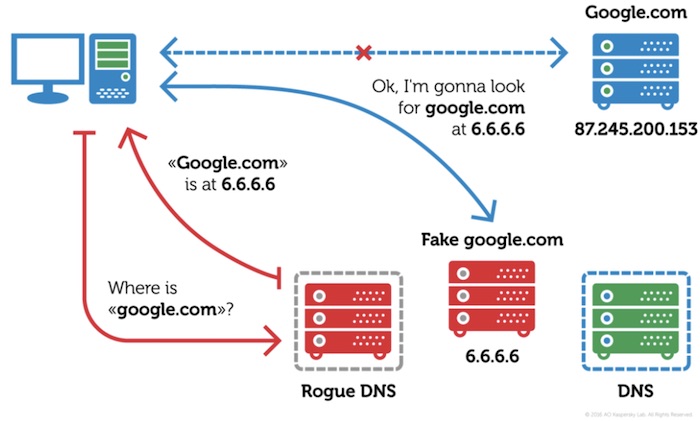
Switcher performs a brute force attack and guesses the password of the router’s web interface. Just in case it’s successful, the trojan changes the DNS server addresses stored in router’s settings.
This step reroutes all DNS queries from the devices in compromised network to the servers of hackers. It’s also known as DNS-hijacking.
Two versions of Trojan.AndroidOS.Switcher malware
The security researchers have identified two versions of Switcher malware. The first version, with package name com.baidu.com, pretends to be a mobile client for the Chinese search giant Baidu.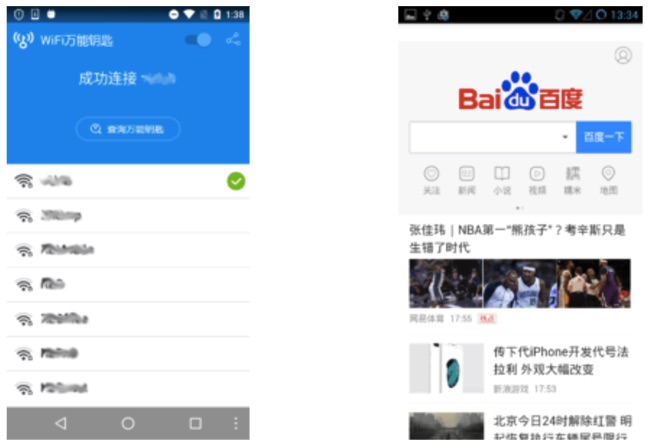
The second version, named com.snda.wifi, disguises itself as a version of a popular Chinese app that shares Wi-Fi information between the users.
The cyber criminals have even created a website that distributes and advertises these fake apps. Also, the web server of the website and malware’s C&C server are the same.
Rogue DNS settings survive even a reboot of the router
Due to the DNS-hijacking, a victim will be fooled into communicating with an entirely new network, which can take you to a fake Google or Facebook. Also, by targeting the entire network, all its users are exposed to a wide range of attacks. It’s also worrying to see that the changed settings won’t be changed even after a reboot.
You can read more details about the malware on Kaspersky’s blog.
Search for these rogue DNS servers
You are advised to check your DNS settings and search for these rogue DNS servers. If you find one of these, alert your ISP or owner of Wi-Fi network:
- 101.200.147.153
- 112.33.13.11
- 120.76.249.59
Did you find this story on Switcher malware helpful? Don’t forget to share your views and feedback.
Also Read: Rakos Malware Is Infecting Linux Servers And IoT Devices To Build Botnet Army