Beware! This Is The Smartest Gmail Phishing Attack You’ll Ever Encounter
Short Bytes: Gmail phishing is one of most common methods used by hackers to compromise the online security of naive users. But, a recent Gmail phishing attack, uncovered by Wordfence, mimics your past conversations and attachments, succeeding in fooling even the tech-savvy netizens. To counter this attack, users should make sure to verify the https:// protocol and hostname in the address bar.
For many of us, getting our Gmail accounts hacked would mean the endgame. It’s the path that helps the hackers to gain the ultimate access to our digital lives. By doing so, one can access our personal identifying information, take control of our online accounts, and whatnot. That’s why, at Fossbytes, we try to explain such security risks often in a very simple language to reach out to the maximum number of users.Today, I’m going to tell you about a Gmail phishing technique that’s being used by the cyber criminals with high effectiveness. Uncovered by Wordfence, this technique has gained wide popularity in the past year. And, over the course of past few weeks, we’ve read reports of even the tech-savvy users being hit by this.
How does this scary Gmail phishing attack work?
This phishing attack first compromises a victim’s Gmail account and starts sniffing the contact list. Then, it sends fake emails, which look very much legitimate, to everyone.
Now comes the smart part — the attack scans the user’s Gmail history and finds the file names of the sent attachments. Then, it applies the same name to the new attachments that appear to be PDFs. However, they are images that send the user to phishing web pages. To make the overall scheme more convincing, the attack steals subject lines from previous emails.
On clicking the attachments, a new tab opens up and you are asked to sign in Gmail again on a fully-functional sign-in page.
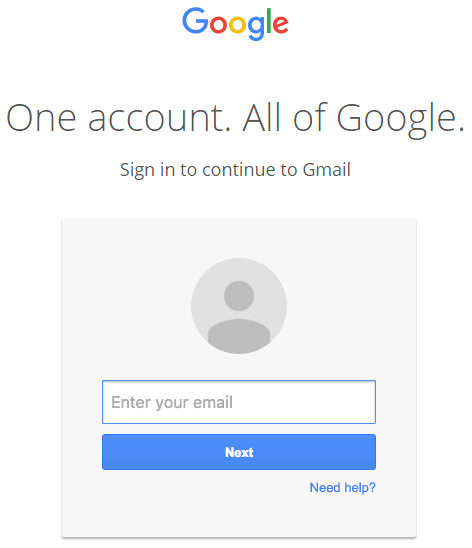
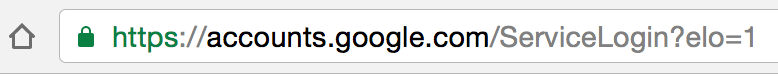
As you can see in the picture below, the URL even has accounts.google.com. Just in case one enters the credentials here, the account gets compromised.
![]() After this, the attacker has the complete control over your email account, and he/she can use it to compromise a variety of services.
After this, the attacker has the complete control over your email account, and he/she can use it to compromise a variety of services.
The experienced users often look at the URL of a page to get an idea of its validity. The victims often find accounts.google.com in the URL and become carefree.
But, they needed to look for another thing in the URL. Such phishing techniques often use a data URL to include a file in the address bar of your browser. You might see data:text.html…. in the address bar. It’s a very large text string, actually a file, that creates a fake Gmail login page.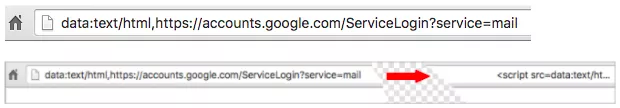
How to defeat Gmail phishing attack?
To make your accounts extra secure, you are also advised to enable two-factor authentication. The users also need to take security checks to ensure the integrity of their online accounts.
In a response to WordFence, who brought the attack into the limelight, Google has issued an ignorant statement that says — “If the users pay no attention to the address bar, phishing and spoofing attack are – obviously – trivial.”
As this attack vector has managed to fool even the experienced users, please share it your friends and family to keep them safe.
Also Read: Student Hacker Infects 16,000 Computers With Spyware, Faces 10 Years In Prison