Petya Ransomware: Another “WannaCry” Is Spreading Globally At A Massive Pace
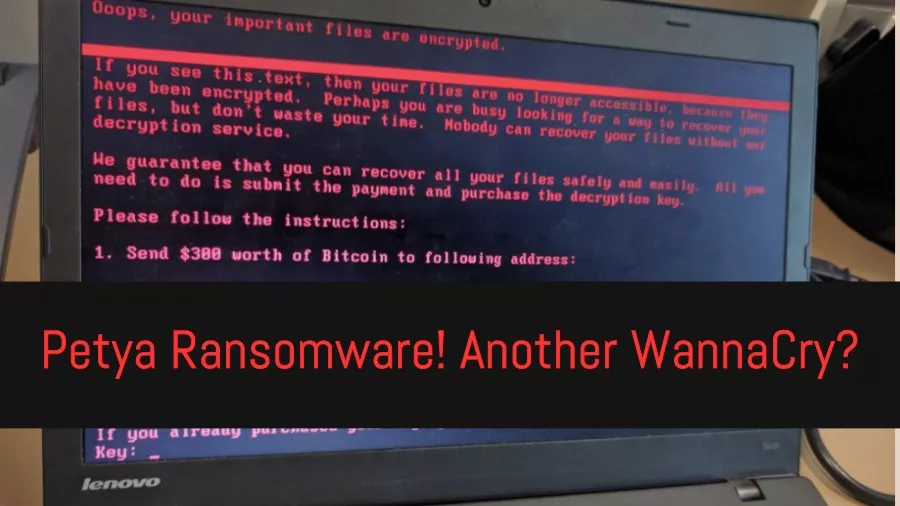
Short Bytes: After WannaCry, a new ransomware threat named Petya is here to haunt your computers. It has already affected a large number of countries, including Ukraine, Russia, Poland, Germany, etc. The malware uses the NSA’s Eternal Blue exploit, which was leaked by Shadow Brokers. The actors behind this threat are demanding $300 in bitcoins as ransom.
Some weeks ago, the WannaCry ransomware spread at a fast pace and infected hundreds and thousands of computers all across the world. Now, another ransomware is busy wrecking havoc. The new attack has taken Ukraine banks offline, resulting in the locking of computer systems in government offices. This ransomware attack has also affected the Chernobyl nuclear plant as well as Ukraine’s electricity supplier. It has also affected the Danish shipping company Maersk, Russian oil company Rosneft.Recommended: 8 Best Anti Ransomware Tools You Must Be Using In 2017
According to Kaspersky’s Costin Raiu, about 60% infections have been recorded in Ukraine, followed by 30% in Russia. The other countries affected by Petya are USA, Poland, Germany, UK, and France.
A supermarket in Ukraine.
The country is under cyberattack.
via @golub pic.twitter.com/jETUuCPcqn— вареничок.еріставі 🇺🇦🏳️🌈 (@maksymeristavi) June 27, 2017
The Petya ransomware is associated with a Bitcoin wallet and demands $300 in Bitcoins for decryption. So far, according to Kaspersky, 7 payments have been associated with this ransomware. According to Symantec, the number of payments are 9.
The latest from @kaspersky researchers on #Petya: it’s actually #NotPetya pic.twitter.com/uTVBUul8Yt
— Kaspersky (@kaspersky) June 27, 2017
What is Petya ransomware?
Kaspersky’s earlier report suggested that the new virus is a variant of the older Petya ransomware. However, the company later clarified that it’s an entirely new infection; that’s why they called it “NotPetya.”
Avira and Symantec have confirmed that Petya is using the Eternal Blue exploit, just like WannaCry. For those who don’t, Eternal Blue exploit targets Windows SMB file-sharing system and spreads quickly between different systems.
Symantec analysts have confirmed #Petya #ransomware, like #WannaCry, is using #EternalBlue exploit to spread
— Threat Intelligence (@threatintel) June 27, 2017
After infection, the affected systems show text: “If you see this text, then your files are no longer accessible because they are encrypted. Perhaps you are busy looking for a way to recover your files, but don’t waste your time. Nobody can recover your files without our decryption service.”
It should be noted that unlike traditional ransomware, Petya doesn’t encrypt all the files at once. It reboots the computers of victims and encrypts the hard drive’s complete Master File Table and makes the Master Boot Record unusable.
Here are some suggestions from security firm F-Secure to safeguard your computers. Apart from these, apply the MS17-010 patch that protected systems against EternalBlue.
Suggestions on what to do if you're infected by #Petya ransomware pic.twitter.com/t2dDcXhEld
— WithSecure™ (@WithSecure) June 27, 2017
Did you find this article on Petya ransomware useful? Don’t forget to share your views.
Also Read: 8 Best Anti Ransomware Tools You Must Be Using In 2017






