Here’s How This Web Page Sniffs Anyone’s Browser History Using Sniffly Attack
 Short Bytes: By abusing the HTTP policies of your web browser, a security engineer has devised a new technique to sniff the browsing history. Using Sniffly and HSTS timing attack, an arbitrary website can violate the privacy of its users. Read ahead to more about how it’s done in detail.
Short Bytes: By abusing the HTTP policies of your web browser, a security engineer has devised a new technique to sniff the browsing history. Using Sniffly and HSTS timing attack, an arbitrary website can violate the privacy of its users. Read ahead to more about how it’s done in detail.
Today tracking the web users is something that website owners do very often using malware injection, cookies, enforcing paywalls and malicious ad scripts. Well, there’s a new technique using the browser fingerprinting is in town. In a demonstration at ToorCon 2015, Yan Zhu, a privacy engineer, showed how to do this and the working of Sniffly attack.
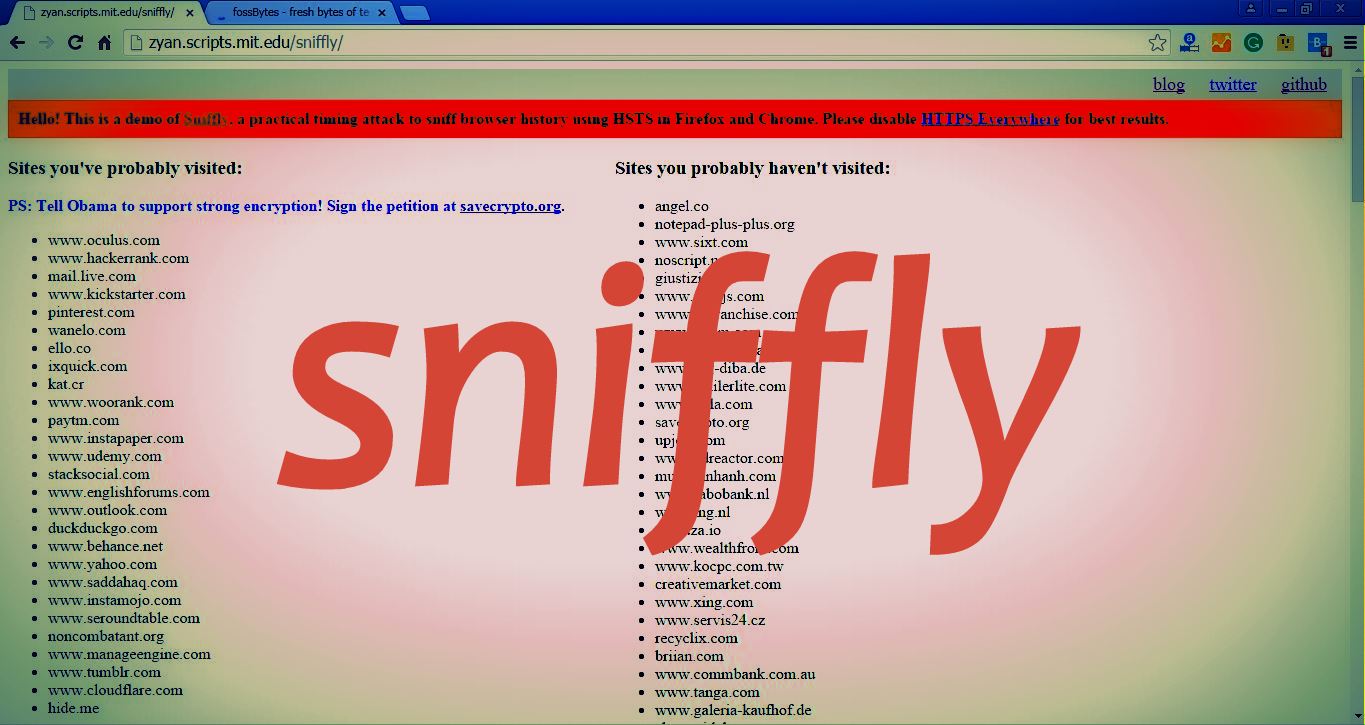
To showcase the demo, Yan has made a web page https://zyan.scripts.mit.edu/sniffly/. You can visit it in Firefox/Chrome/Opera with HTTPS everywhere and see how Sniffly digs your browsing history in the left column.
Here’s how Sniffly works:
When you visit the Sniffly page, your web browser tries to load the images from various HSTS domains over HTTP. Sniffly sets a CSP policy that restricts images to HTTP, so that image sources are redirected to HTTPS.
Also read: What is Traffic Fingerprinting and How it is Used to Attack Tor Network
When an image is blocked by CSP, the time taken for the image to be redirected from HTTP to HTTPS is calculated. If the time is of the order of a millisecond, it means no network request was made and it was HSTS redirect. This implies that the user had earlier visited this domain.
However, if the time the taken to redirect the request is of the order of 100 milliseconds, it means the user hasn’t visited the domain before as a network request probably occurred.
The Sniffly attack is allowed if you visit a site that supports HSTS, it can sniff your browsing history by measuring the redirect time.
To know more about the Sniffly attack, visit the Yan’s GitHub page.
Get White Hat Security Hacker Bundle
[adinserter block=”12″][adinserter block=”13″]






