This Hacker is Destroying Racist and Homophobic Websites One by One
Short Bytes: A hacker that operates a Twitter handle named Amped Attacks, is taking down the…

Short Bytes: A hacker that operates a Twitter handle named Amped Attacks, is taking down the…

Short Bytes: A security researchers from the Pen Testers Partners has revealed that the smart iKettles…
Short Bytes: To make your favorite social network more secure, Facebook is now sending out notifications…
Short Bytes: According to the latest revelations made by the American law enforcement agencies, ISIS terrorists…
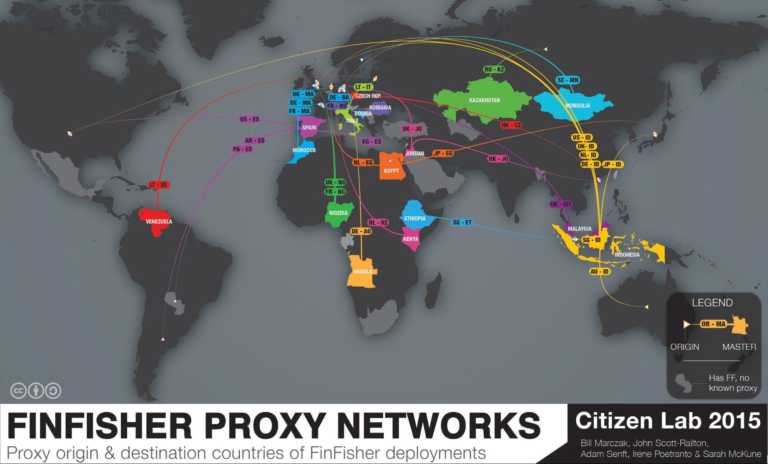
Short Bytes: In 2015, the infamous spyware FinFisher is spread in 32 countries to perform advanced citizen…

Short Bytes: Visual Hacking is a security threat that is often overlooked by us. This is…

Short Bytes: In the third article of the “Steps to Effective Security” series, I’ll tell you…

Short Bytes: The Chinese government has taken an unprecedented step to comply with a U.S. request and…

Short Bytes: DuckDuckGo CEO Gabriel Weinberg takes a dig at Google in his AMA session saying,…

Short Bytes: To keep your WhatsApp data safe and encrypted, WhatsApp has partnered with Google Drive. Take…