Arbor Networks Report: Largest DDoS Attack Of 579Gbps In The First Half Of 2016
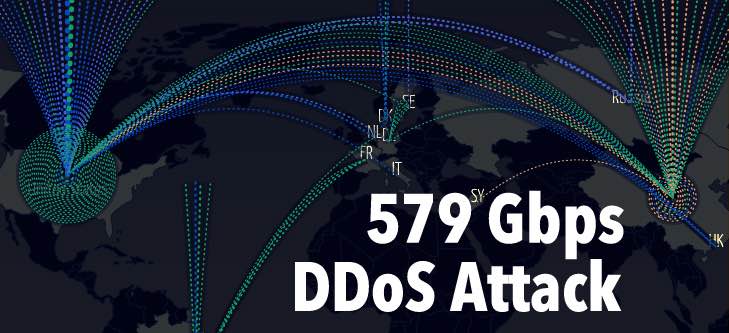
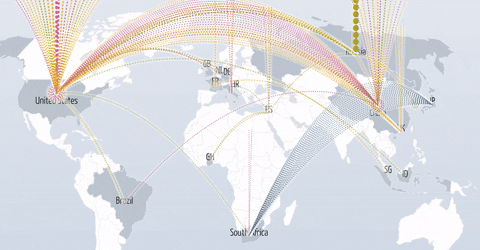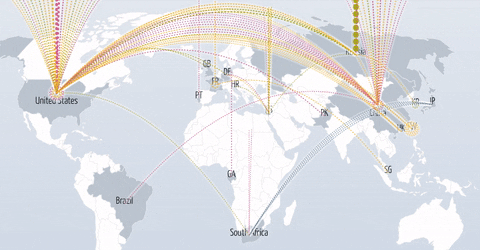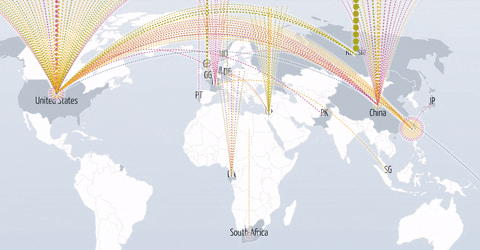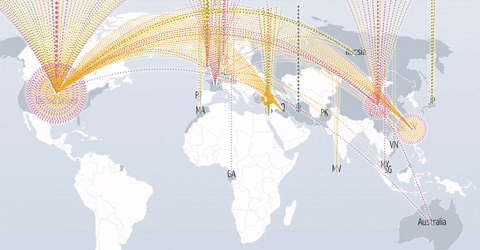 Short Bytes: Arbor Networks has published the statistics of the DDoS attacks in the first half of 2016. The largest one went up to 579Gbps. An interactive map shows the DDoS attacks made on a global level.
Short Bytes: Arbor Networks has published the statistics of the DDoS attacks in the first half of 2016. The largest one went up to 579Gbps. An interactive map shows the DDoS attacks made on a global level.
In this article, we’ll be narrowing ourselves to the information about DDoS attacks. Arbor Networks, a subsidiary of NETSCOUT, has published the global DDoS attack statistics report for the first half of the year 2016.
The size and the number of DDoS attacks have proliferated in the last couple of years. This can be accredited to the ease of access when it comes to obtaining resources, mostly available for free, to initiate an attack. Arbor Networks Inc. uses its homegrown partnership platform ATLAS (Active Threat Level Analysis System) to harvest anonymous traffic data related to the DDoS attacks. This data is then used to create an interactive Digital Attack Map.
The largest DDoS attack touched a new high of 579Gbps, an increase of 73% from the largest attack recorded in 2015. In January, we told you about a hacker group claimed a 600Gbps attack on BBC surpassing the then 334Gbps highest record observed by Arbor. The claim was never confirmed so the 579Gbps attack currently tops the chart.
A slight increase in the number of big attacks is also visible. In 2015, the number of attacks over 100Gbps was 223, while it is 274 for the first half of 2016. Taking attacks over 200Gbps into account, 16 attacks were observed in 2015 while the number has jumped to 46 in the first half.
The Arbor Networks chief security technologist Darren Anstee says that the average size of 80% of the DDoS attacks was below 1Gbps in the first half and 90% of them didn’t even last for an hour. “On-premise protection provides the rapid reaction needed and is key against “low and slow” application-layer attacks, as well as state exhaustion attacks targeting infrastructures such as firewalls and IPS.”
Many of the bigger attacks didn’t require brainstorming techniques. The Linux-driven LizardStresser IoT botnet and its implementation were the honeycombs for many of the evil-minded bees. Simple to compile and run tool was the backbone of a large 400Gbps attack targeting gaming website on a global level.
The advent of the leap year did bring some new goodies for the wannabe attackers, the Reflection Amplification Technique using DNS servers. Earlier, the NTP and SSDP protocols were used for the reflection amplification but the implementation of DNS was prominent in the first half of 2016. Also, the identity of the original source of the attack can be made concealed using this technique.
Click here to know more about the DDoS attack report.
If you have something to add, tell us in the comments below.
Also Read: How DDoS Attack Works?