What Are The Different Types Of Application Layer Attacks?

 Short Bytes: Application layer attacks are the most favored ways of launching an attack. It just needs a little modification in the code and a little tweak before it can start sending information to the hacker.
Short Bytes: Application layer attacks are the most favored ways of launching an attack. It just needs a little modification in the code and a little tweak before it can start sending information to the hacker.
A person with even a little bit of programming knowledge can use these techniques to hack into a system or software. Here are some of the ways which are well known for the application layer attacks:
Exploiting a weakness in the software:
One of the most common methods of launching application layer attacks is to exploit the software-level weaknesses commonly found on servers. Some of these weaknesses are pertaining to Sendmail, PostScript, and FTP.
Once you have exploited these weaknesses, you can easily get access to a computer with the account-level permissions running the application.
Trojan Horse — Application layer attacks:
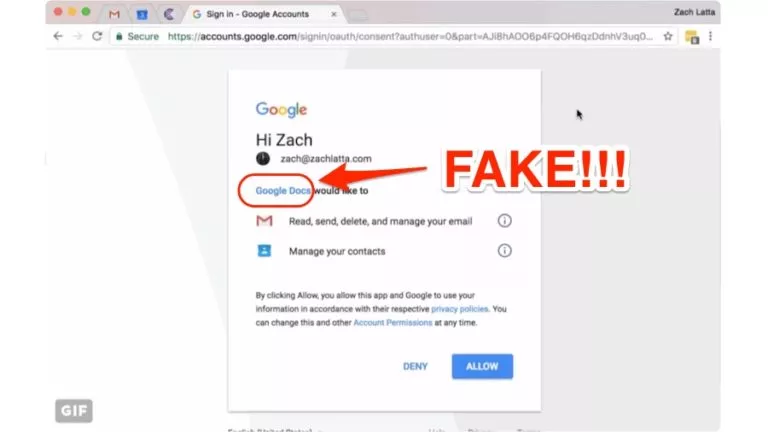
Trojan horses are nothing but the fake programs which pretend to be the original programs. Since they can replicate most of the application level behavior of an application, a trojan horse is one of the of the most famous styles to launch application layer attacks. You can read our dedicated article on differences between virus, trojan, malware etc.
Besides providing the functionalities of a normal application, a trojan horse also contains other features which work in the background such as monitoring login to capture password and other sensitive data information like credit card details, etc.
In the background, a trojan horse keeps sending the sensitive information to the attacker. If you want, you can also modify application functionality to exploit more such as applying a bcc to all e-mails etc.
Exploiting HTML, HTTP, and web browser technology:
These forms of application layer attacks are the newest ones. These attacks basically exploit the overt nature of the new technologies such as HTMP, web browsers, HTTP etc.
These application layer attacks mostly include Java applets and ActiveX controls. A powerful harmful program is passed in the network and loaded in the user’s browser.
Active X to Trojan Horse:
This is an advanced version of the above step. Hackers use ActiveX controls to make them act as trojan horses. This technique uses VBScript. Using this technique, you can overwrite files and even execute other programs.
One of the most important aspects of these new attacks is that they are not initiated by the attacker, but by the user. A user basically selects an HTML page with harmful applet or script and runs it.
Furthermore, due to the portable nature of the programming language, they are not restricted to a particular OS or hardware.
Did you find the article helpful? Let us know in comments below.