Indian Developer Grabs $100,000 For Reporting ‘Sign in with Apple’ Flaw
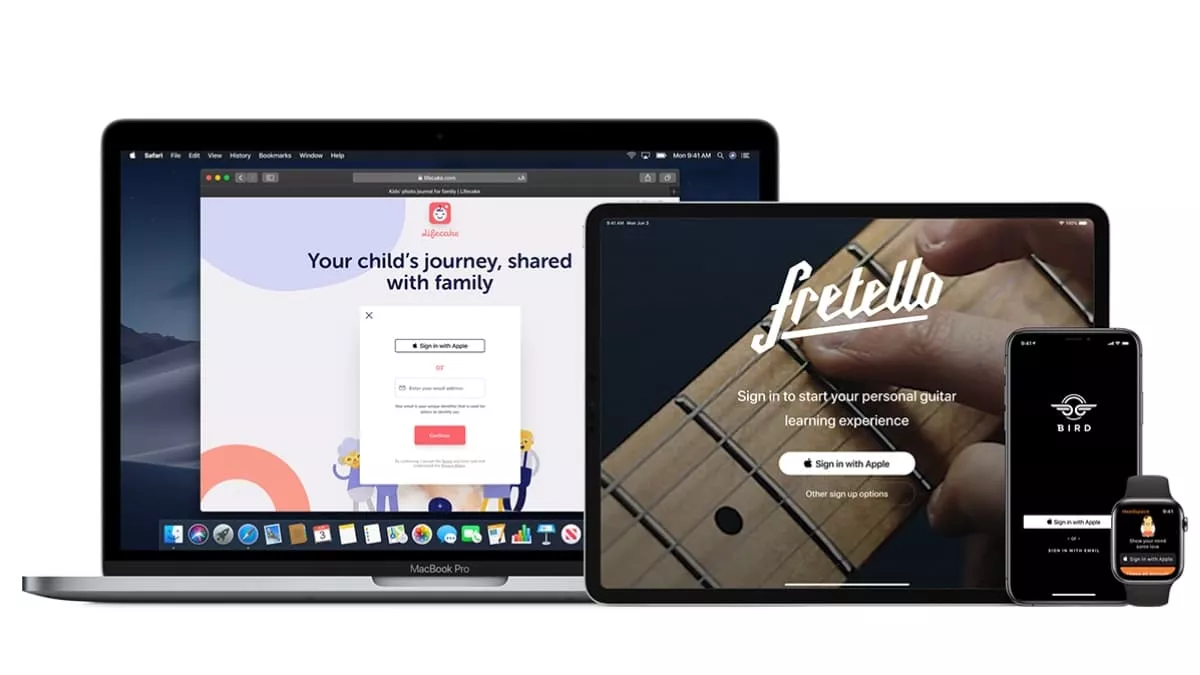
Sign in with Apple is similar to other app login options such as “Sign in with Google” or Facebook; however, the difference is that Apple’s single sign-on offering is more private and even allows users to mask their email ID.
But Apple’s login method was hoarding a severe zero-day vulnerability that could have resulted in hackers taking over user accounts.
The bug was spotted back in April by an Indian developer, Bhavuk Jain, for which he received a whopping $100,000 in bug bounty. Thankfully, Apple has patched the vulnerability and says no accounts have been compromised.
According to Jain, the bug was specific to third-party apps, i.e., it only affected people who tried using “Sign in with Apple” in a third-party app.
Jain explains in his blogpost that the Apple login method authenticates a user either via JWT (JSON Web Token) or a code generated by Apple’s server. However, Jain noted that attackers could have forged a token linked to any email and could have verified it using Apple’s public key.
If the bug hadn’t been discovered, a hacker could have enjoyed a “full account takeover” despite a user masking their email.
Apple introduced “Sign in with Apple” back in 2019 and brought the feature along with iOS 13. The best part about the feature is that a user can control the amount of data to be shared with an app.