Intel x86 Processors Come With A Secret Backdoor That Nobody Can Fix

 Short Bytes: A security researcher has outlined a dangerous loophole that affects the Intel CPUs that have Intel Management Engine and vPro enabled. While there’s no known exploit at the moment that uses this flaw, it can act as a powerful rootkit mechanism.
Short Bytes: A security researcher has outlined a dangerous loophole that affects the Intel CPUs that have Intel Management Engine and vPro enabled. While there’s no known exploit at the moment that uses this flaw, it can act as a powerful rootkit mechanism.
Some of you might be aware of the Intel Management Engine (ME), a subsystem that is basically a 32-bit ARC microprocessor. It’s located inside the processor and controls the main CPU.
In low power states, ME can function independently. On some chipsets, the ME firmware implements a system called Active Management Technology (AMT), which provides a way to manage the CPU remotely. The AMT system is implemented on Intel CPUs that come with vPro technology.
To do this management task, ME has the power to gain access to any memory region without the need of any permission given by the main CPU.
This task is also aided by a TCP/IP server that has the ability to bypass any firewall on your computer. The main focus of this implementation is enterprises that manage multiple systems remotely.
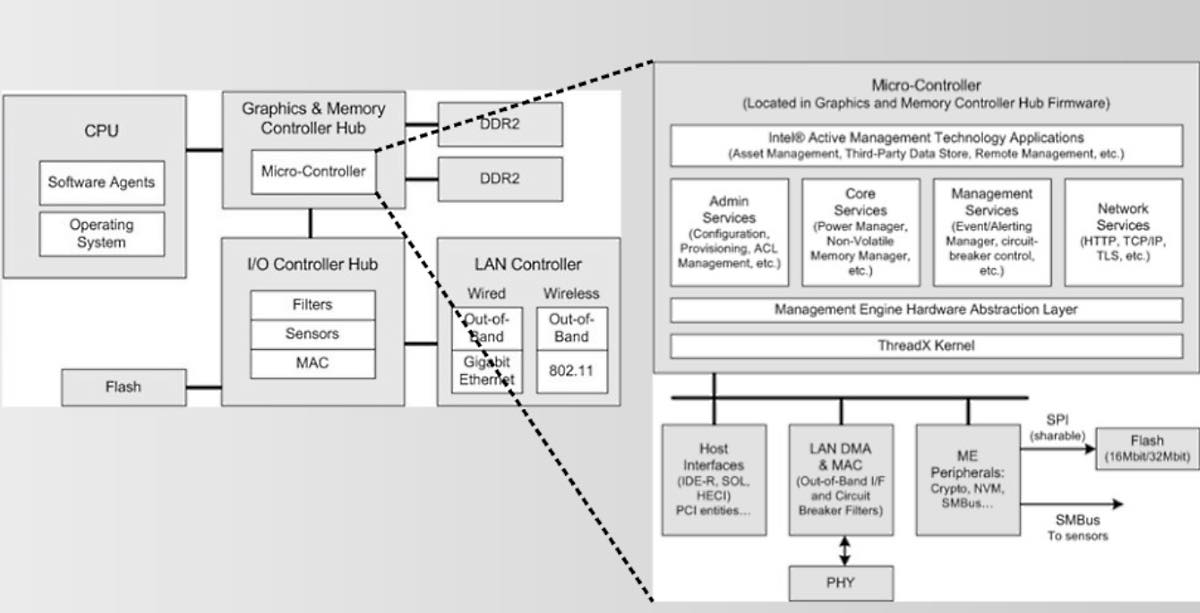
Zammit outlines further details in his article and labels Intel’s remote management technology as insecure. Intel itself has revealed very little about the functions and security systems deployed around this ME.
Even though ME firmware is protected cryptographically, the researchers have managed to exploit weaknesses in the firmware and taken control of the ME.
In a bigger picture, Intel ME can act as a powerful rootkit mechanism. It a well-known fact that attackers can easily gain access to a system that’s compromised by a rootkit.
Interestingly, this flaw is independent of the operating systems. This means that it affects all PCs–Windows, Mac, Linux–that have both IME and vPro enabled.
However, at the moment, there’s no known exploit that can be used. Also, it’s a very tiresome job to break the RSA 2048 encryption on a chip.
Zammit says that he doesn’t aim to replace or remove Intel’s ME. Instead, he supports an open source approach and advocates a “completely libre soft replacement for ME firmware.”
Did you find this article helpful? Don’t forget to drop your feedback in the comments section below.
Also Read: How To Hack Anyone’s Facebook Account With Their Phone Number