Hackers Can Steal Data By Tweaking Monitor’s Brightness By Just 3%

As weird and creepy as it may sound, researchers have invented a technique to steal your data by tweaking the brightness of your PC’s monitor by merely 3%.
In a paper published by the researchers from the Ben-Gurion University of the Negrev, Isreal has demonstrated how Air-gapped computers can be exploited to retrieve data by simply meddling with the brightness of the monitor by a percentage that will usually go unnoticed.
Air-gapped computers are workstations that are kept isolated from the internet and other internet-connected computers to safeguard the data stored in them.
The researchers introduced an optical covert channel through which the sensitive data is concealed on the LCD screen brightness in a covert way, which is invisible to users. The technique works even when the person is using the PC.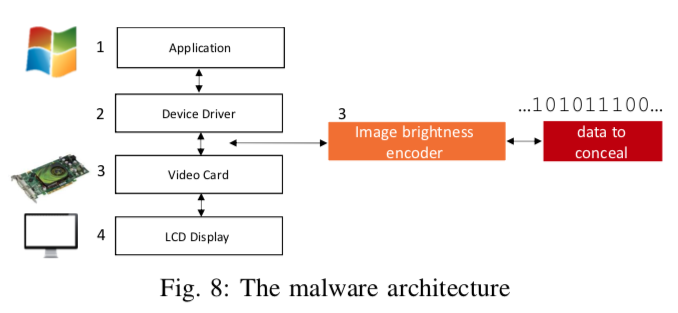
The attack model consists of the following stages:
- In the first stage, researchers contaminated the target network by introducing a piece of malware or a modern advanced persistent threat (APT)
- Modulating the captured data on the monitor by encoding it as a stream of bytes. Researchers assigned a value “1” to a certain brightness level on the monitor and “0” to another brightness level.
- When the screen brightness is quickly changed, it generates a sequence of bits on the display.
- In the last stage of the attack, a camera is deployed that could take the recording of the target computer’s display. Researchers then proposed that image processing techniques could be used for reconstructing the sensitive information from the recording.
If you’re thinking that constantly changing brightness of the screen might attract suspicion from the user, researchers found that the technique works flawlessly even when the red color of each pixel is changed by just 3%. Such a trivial change in the brightness would be invisible to a naked human eye but could be captured by a camera.
Thankfully, this attack has two pre-requisites that are hard to fulfill, thus keeping it out of the hands of ordinary cybercriminals. First, the malware has to be planted physically on the air-gapped target computer, and second, the hacker would have to find a way to infiltrate the security cameras or webcams near the target PC to record the modulated data.
You can read more about this research in the detailed research paper titled “Leaking Sensitive Data from Air-Gapped Workstations via Screen Brightness.”