USB Thief — This Self-projecting USB Trojan Can Give You Nightmares

 Short Bytes: Security researchers have identified a new malware named USB Thief that has the ability to steal data from air-gapped computers without leaving its trace. The malware uses a unique method of protecting itself with AES128-encryption and renaming the files in each new instance.
Short Bytes: Security researchers have identified a new malware named USB Thief that has the ability to steal data from air-gapped computers without leaving its trace. The malware uses a unique method of protecting itself with AES128-encryption and renaming the files in each new instance.
Imagine a malware that spreads through USB drives, steals your computer’s data and goes undetected. Sounds like a bitter pill to swallow? Well, security researchers have spotted this unique data-stealing trojan in the wild that comes with self-protection mechanism that protects it from being reproduced or copied.
The researchers at ESET security firm have unveiled the fact that Win32/PSW.Stealer.NAI malware, or USB Thief, can attack the isolated or air-gapped computers. Each attack of this malware relies on a USB device and it leaves no evidence on its target.
How does USB Thief spread in the wild?
Instead of spreading via the tried-and-tested techniques of autorun files and shortcuts to run itself, USB Thief uses another technique that involves using itself in the portable versions of popular application like NotePad++, Firefox web browser, and TrueCrypt on thumb drives.
This queer fish takes advantage of this disguise and finds home in the command chain of such applications in the form of a dynamically linked library or a plugin. As a result, whenever the target runs the applications, the malware also runs in the background.
The protection mechanism of USB Thief
The USB Thief malware contains six files — four executables and two containing configuration data. Talking about its self-protection techniques, the malware uses two methods:
- Some of the files are protected by AES128-encryption.
- The filenames are generated with some cryptographic jugglery that makes the filenames different for every instance of malware.
The researchers found it very challenging to crack this dish fit for hacking Gods. Here’s is the execution flow of malware explained in a flow-chart. The malware operates with 3 payloads that interact with two configuration files and implements the data stealing functionality with the payload.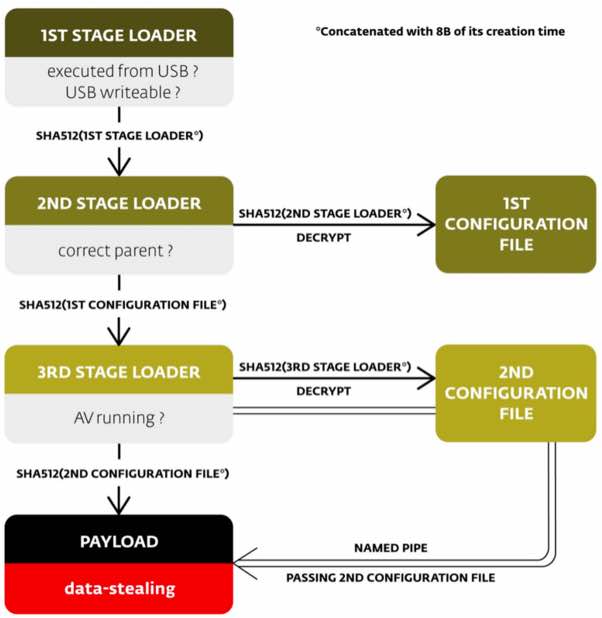
At the moment, the USB Thief malware is not widespread but its ability to be used in targeted attacks on isolated computers makes it the black sheep of the malware family. fossBytes advises you to turn of Autorun feature in your computer and do not use USB drive from random sources.
— ESET
You’ll find these interesting:






