Forget KRACK Attack, 5 Year Old Encryption Bug Returns For Google And Microsoft
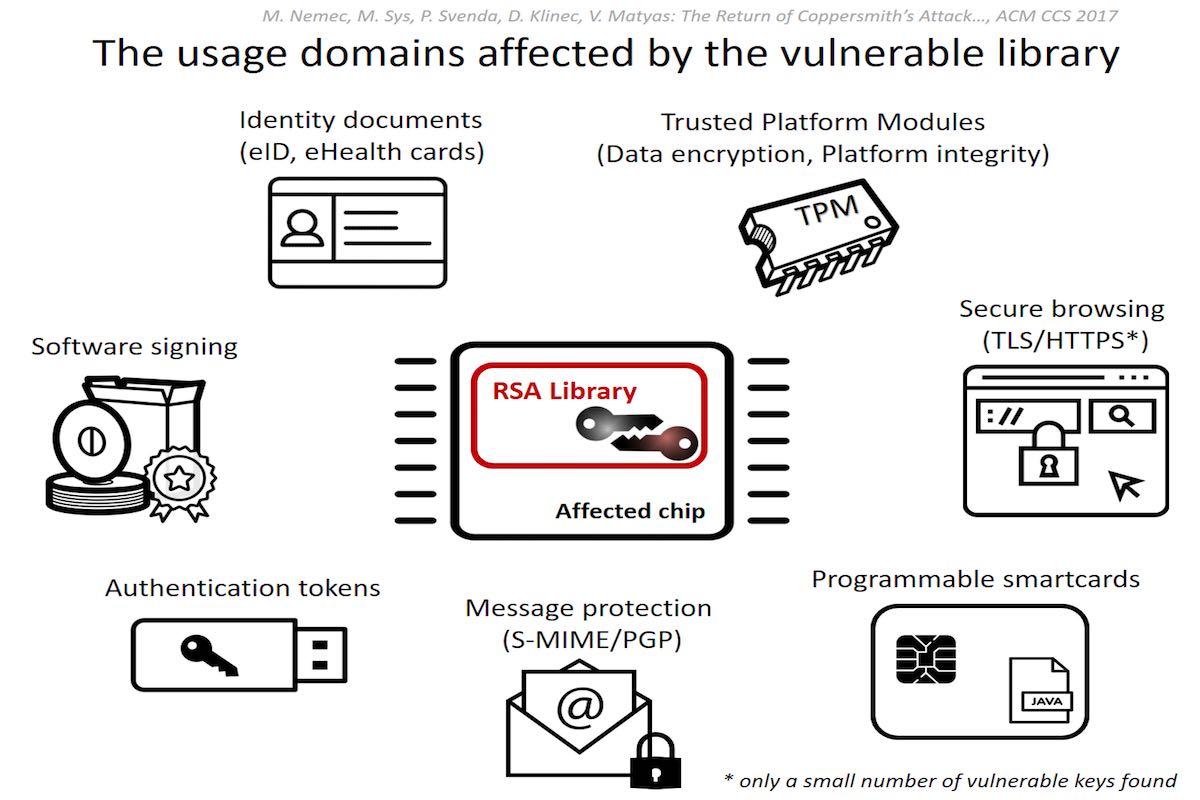
The ROCA hack: Vulnerable RSA Generation (CVE-2017-15361), developed by the researchers at Centre for Research on Cryptography and Security, Masaryk University, Enigma Bridge and Ca’ Foscari University targets the weakness in the cryptography tech in chips made by Infineon Technologies.
The range of affected devices – released as early as – includes a large number of Chromebooks, and Windows laptops manufactured by Fujitsu, HP, and Lenovo which feature the hardware chips created by Infineon.
Read Our Coverage on KRACK attack here
The problem lies in the way the manufacturers implement the widely-used RSA encryption. This makes it possible to figure out the private key if the public key is available which isn’t a big deal.
“The currently confirmed number of vulnerable keys found is about 760,000 but possibly up to two to three magnitudes more are vulnerable,” warn the researchers. They will present their paper at the ACM Conference on Computer and Communications this month where the Krack attack will also be on display.
ROCA hack is practically more effective against 1024-bit encryption keys. Researchers calculated the cost of performing the attack via Amazon cloud servers. It would require around $76 to crack a 1024-bit key while more funds would be needed for a 2048-bit key. It would cost $40,000 as higher bit keys are more complicated, and therefore, harder to crack.
Jake Williams, an ex-NSA staffer and the owner of the cybersecurity company RenditionSec, calls ROCA issue more severe than KRACK, Forbes reports. Williams suggests two ROCA attack scenarios; one involves the attacker compromising the digital signature certificate used to validate a software’s source. An attack can use the published public key to reverse engineer the private key to sign the software and impersonate the victim.
Second, the attacker can run malicious code by fooling the Trusted Platform Module (TPM) chip which stores the RSA encryption keys.
“The TPM is used to ensure the code used to boot the kernel is valid. Bypassing a TPM could allow the attacker to perform an inception style attack where they virtualize the host operating system,” he said.
“There are dozens of other variations of attacks, but these Infineon chips are huge in hardware security modules (HSMs) and TPMs”
The vulnerability was first spotted in January this year, and Infineon was notified in February. The researcher had an agreement to wait for 8 months before making it public. Software updates and mitigation guidelines have been released by Microsoft, Google, HP Lenovo, Fujitsu. Researchers have provided detection tools to check whether the keys are vulnerable.
Read the detailed post by the researchers to know more about the ROCA attack.
Also Read: Russia Plans To Launch Its National Cryptocurrency Called “CryptoRuble”