Any PC Manufactured Before 2019 Is Vulnerable To ‘Thunderspy’ Attack
Björn Ruytenberg, a security researcher from Eindhoven University of Technology, has revealed that all the PCs manufactured before 2019 could be hacked, thanks to a flaw in commonly used Thunderbolt port. Thankfully, exploiting the flaw requires physical access to your device.
Dubbed “Thunderspy”, the attack could allow a hacker to read and copy all the data from your PC even if it is in sleep mode or locked. Moreover, it can also steal data from encrypted drives.
Last year, a group of security researchers discovered a group of flaws in the Intel’s Thunderbolt port found in a majority of PCs. The collection of flaws known as Thunderclap could be exploited by connecting a tailored device to the vulnerable computers to access all the data.
The researchers, then, advised users to use a Thunderbolt feature called ‘security levels’ that turns the port into a mere USB and display port by disabling access to untrusted devices connected to the port.
Now, Ruytenberg has discovered a new technique that makes ‘security levels’ ineffective by modifying the firmware of the internal chip through the ‘Thunderspy’ attack.
At the time of suggesting ‘security levels’ to mitigate the risk when Thunderclap was discovered, Intel also added an additional security mechanism called Kernel Direct Memory Access Protection that could prevent Ruytenberg’s new technique.
However, it has been found that kernel DMA is found only in a handful of PCs manufactured in 2019 or before as it is not an industry-standard yet. Researchers found out that there are no Dell-manufactured PCs with kernel DMA and only a few Lenovo and HP models manufactured in 2019 or before that are equipped with DMA.
You can found out whether your PC has Kernel DMA or not by using this tool designed by Ruytenberg himself.
How does Thunderspy attack works?
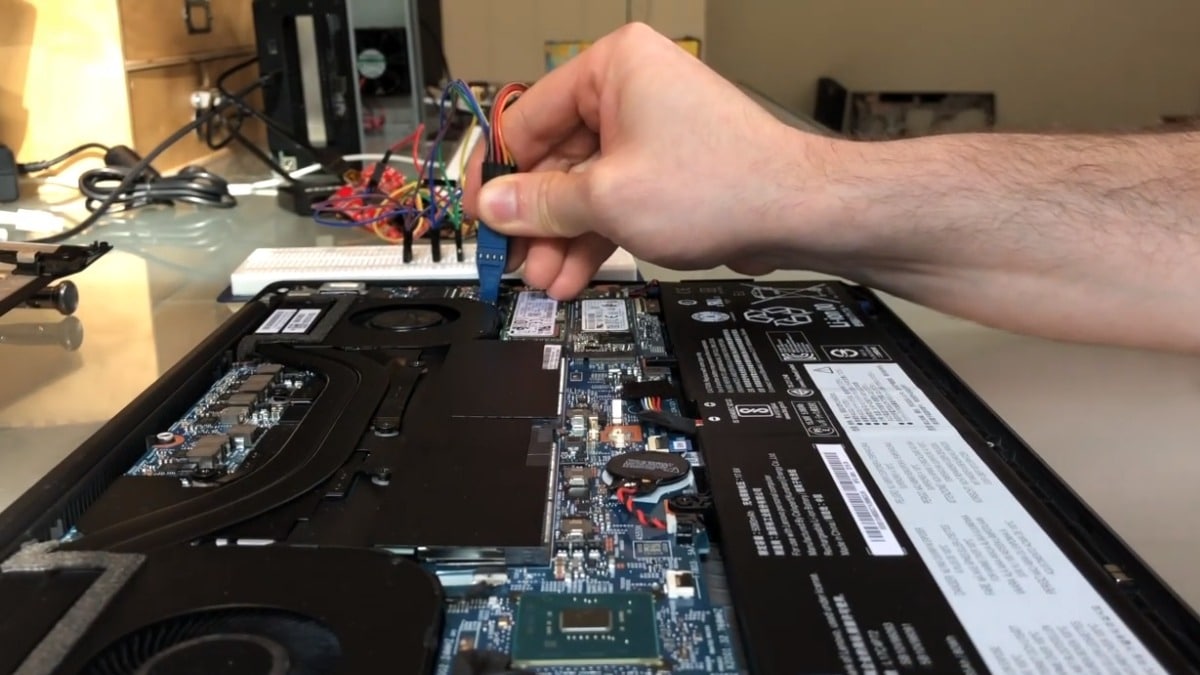
In a video released by Ruytenberg as a PoC demo, he has shown how connecting a SPI programmer device with a SOP8 clip connected to the bottom part of the device could allow anyone to rewrite the firmware of the chip.
The process requires unscrewing the bottom lid to connect the malicious device but takes hardly two minutes to disable all the security settings and access data.
Thunderspy – an evil-maid attack
Thunderspy falls in the category of evil-maid attacks which means it requires physical access to a device to attack it, making it less widely exploited as compared to other attacks that could be executed remotely.
However, Thunderspy is a stealth attack, therefore, the victim would fail to notice that his/her device was tampered with once the attacker is done with the procedure.
Nonetheless, Thunderspy attack makes millions of Windows PCs vulnerable all over the world, and currently, there are no known measures to mitigate the attack as it requires manufacturers to redesign the hardware, Ruytenberg.