NextCry Ransomware Encrypts Files On NextCloud Linux Servers

NextCry ransomware is a new malware that has been spotted in the wild targeting files of clients who use Nextcloud file sync and share service.
The ransomware gets its name from the extension it uses to append the file names of encrypted files. There is no free decryption tool available for NextCry victims at the moment and it remains undetected by the majority of antivirus engines on public scanning platforms.
NextCry Ransomware Spotted
NextCry ransomware surfaced when a NextCloud user named ‘xact64’ took the issue to the Bleeping Computer forum looking for a way to decrypt files.
The user claims that his system was backed up, but the synchronization process started updating files to his laptop with the encrypted version on the server.
He also found that some of his files were renamed to NextCry.
“I realized immediately that my server got hacked and those files got encrypted. The first thing I did was pull the server to limit the damage that was being done (only 50% of my files got encrypted),” says xact64.
How does NextCry work?
According to Bleeping Computer, NextCry ransomware is a Python script compiled in a Linux ELF binary using pyInstaller. It uses the Base64 algorithm to encode the filenames.
One noteworthy aspect of this malware is that it uses the AES-256 algorithm to encrypt the files but the key is encrypted with an RSA-20148 public key embedded in the ransomware code.
After execution, NextCry first searches the victim’s Nextcloud file share and sync data directory by reading the service’s config.php file.
Later, it deletes those folders that could be used to restore files and encrypts all the files in the data directory.
NextCry Exploits The PHP-FPM vulnerability
NextCloud has confirmed that ransomware authors are exploiting the NGINX+php-fpm vulnerability that surfaced some time ago. The file sync and share service had alerted about a remote code execution vulnerability that impacts the default Nextcloud NGINX configuration.
The flaw lies in the PHP-FPM (FastCGI Process Manager) component (CVE-2019-11043) that is used by hosting providers such as Nextcloud in their default setup.
Demands Ransom In Bitcoin
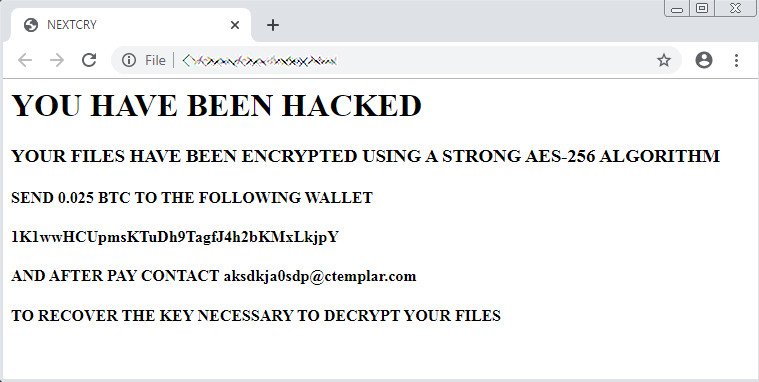
NextCry ransomware demands a ransom of BTC 0.025 (around $210) to decrypt the encrypted files.
Here’s the ransom demand note:
How To Avoid NextCry Ransomware?
While there is no free decryption tool available for NextCry victims, those who use NextCloud services can fix the vulnerability by updating their PHP packages and NGINX configurations.
You can protect your files by upgrading to PHP 7.3.11 or PHP 7.2.24 (depending on the development branch being used).
Also Read: Chinese Hackers Win $382,500 For Hacking KVM On Ubuntu, Edge, Adobe Reader






