LeakerLocker Android Ransomware Threatens To Expose Personal Data To All Your Contacts

Short Bytes: LeakerLocker, an Android ransomware, is here to infect the Android smartphones and threaten the users. This ransomware doesn’t use encryption while locking down your personal data and asks for ransom in return for the release of data. The malicious apps have been removed from Play Store and Google is investigating the issue. Meanwhile, you’re advised to check your phone and remove these apps as soon as possible.
After telling you about the wrath of WannaCry and Petya ransomware on Windows platform, today I’m going to tell you about a similar threat that affects your Android smartphone. Named LeakerLocker, this malware was uncovered by the security researchers at McAfee.The ransomware was found on Google Play. Notably, it doesn’t use encryption for keeping you away from your files and demanding extortion. The researchers have identified it as Android/Ransom.LeakerLocker.A!Pkg.

LeakerLokcer spreading via 2 apps on Google Play
LeakerLocker ransomware is infecting the smartphones of Android users via two applications. Wallpapers Blur HD, the first app, has been downloaded between 5,000-10,000 times. The app was last updated on April 7.

The second malicious application is Booster & Cleaner Pro, which has been downloaded between 1,000-5,000 times. As these apps enjoy a high rating of 3.6 and 4.5, many users have downloaded them without realizing the risks involved.
When executed, the Booster & Cleaner Pro app displays the normal functions of an Android booster app. As it’s a cleaner app, the Android user agrees to grant almost any permission. After the boot, the ransomware initiates the malicious activity and locks the device.
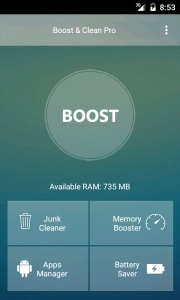
LeakerLocker ransomware reads a victim’s email address, random contacts, browser history, calls, pictures, etc. This information is randomly chosen to display via JavaScript and threat the victim that lots of data has been copied.
After the victim enters the credit card number and hits pay, the malicious code sends a request to the payment URL. If the payment is successful, the message is displayed “our [sic] personal data has been deleted from our servers and your privacy is secured.”
If the payment is failed, it shows “No payment has been made yet. Your privacy is in danger.”
It goes without saying that infected users must not pay as there’s no guarantee that the locked information will be released or they won’t be threatened again. Meanwhile, the malicious apps have been removed from Play Store. You are advised to take a look at your phone and remove these apps and scan your smartphone with a reputable antivirus solution.
Source: McAfee Blog
Also Read: 8 Best Anti Ransomware Tools You Must Be Using In 2017






