DoubleLocker: This Android Ransomware Activates Every Time You Press Home Button
Detected as Android/DoubleLocker.A, this Android ransomware takes inspiration from a banking trojan named Android.BankBot.211.origin, which is distributed with the help of disguised programs. However, instead of compromising users’ banking accounts, DoubleLocker ransomware has a couple of other tricks up its sleeves.
It’s distributed via fake Adobe Flash Player through infected websites. After it’s launched, the fake app requests the activation of malware’s accessibility service, called “Google Play Service.” This enables the malware to gain admin rights and set itself as default home app.
Being the default home app allows the malware to increase its persistence. Every time a user taps the home button, the ransomware gets activated and the device gets locked.
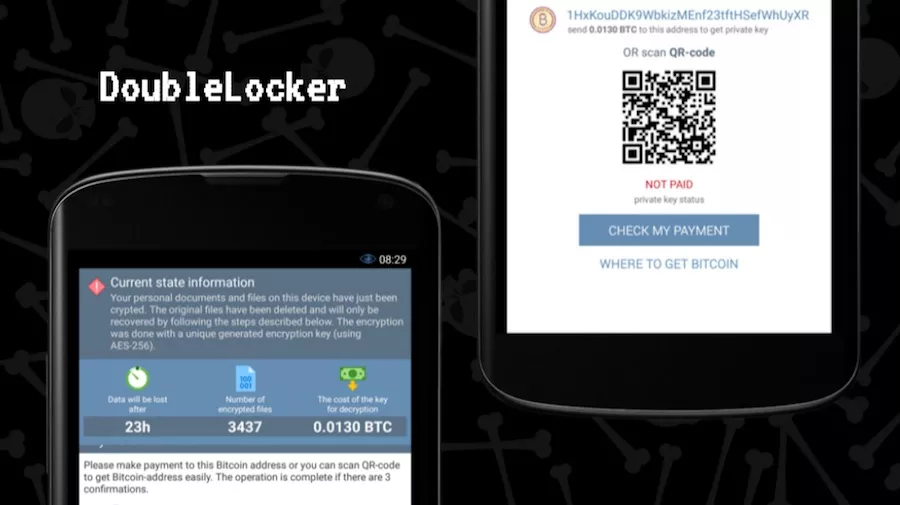
The attackers have set the ransom to 0.0130 bitcoin, which is about $55. The message tells that it must be paid within 24 hours.
The overall operation of DoubleLocker can be further divided into two parts. First, it changes your device’s PIN. Once the ransom is paid, the attacker can reset the PIN and unlock the device.
Second, the ransomware encrypts all files on device’s primary storage using AES encryption. As per the researchers, there’s no way to recover files without the encryption key.
To get rid of DoubleLocker ransomware, the ESET researchers advise the users to perform a factory reset. In case your device is rooted, there is a method to bypass the PIN lock without a reset. You can find further details here.
Did you find this story on DoubleLocker helpful? Don’t forget to share your views with us.
Also Read: 8 Best Anti Ransomware Tools You Must Be Using In 2017






