Ubuntu Linux, Safari, Adobe Reader, And Edge Hacked At Pwn2Own 2017
Short Bytes: At the Trend Micro-sponsored Pwn2Own 2017 competition, the security researchers were able to hack many…

Short Bytes: At the Trend Micro-sponsored Pwn2Own 2017 competition, the security researchers were able to hack many…
Short Bytes: The Edina Police Department is running after an unknown suspect responsible for a wire…

Short Bytes: CUJO is a smart firewall that can connect to your home router via the…

Short Bytes: You’ll be surprised to know that the Dark Web has shrunk at a tremendous…

Short Bytes: WikiLeaks has released the complete catalog of CIA’s hacking tools and malware. This revelation…

Short Bytes: A paper published by an Israeli team of researchers elaborates a new method of…
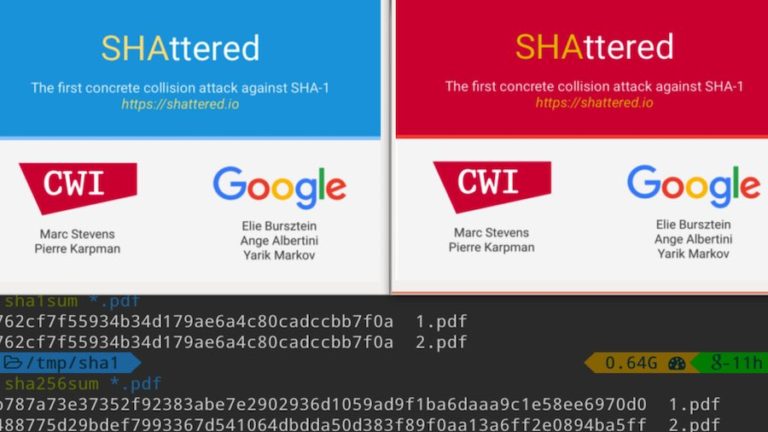
Short Bytes: Google has achieved the first successful SHA-1 collision attack. By creating a specially crafted…

Short Bytes: Juice Jacking is one of the most underrated security threats around. It can be…
Short Bytes: Verify Apps is a cloud-based security feature in the Android operating system. It regularly…

Short Bytes: A new research conducted at the Lehigh University has taken the browser fingerprinting to…