Google Just Broke SHA-1 Encryption — One Of The Most Popular Cryptographic Hash Functions
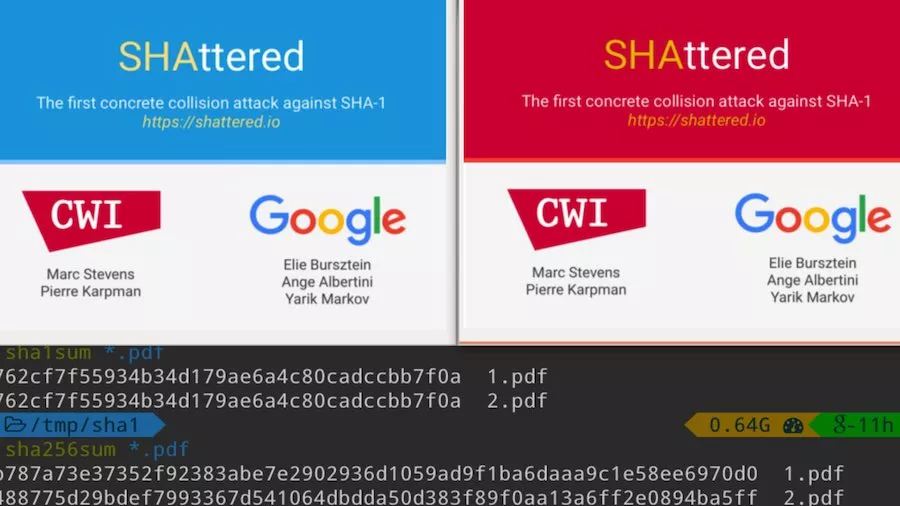
Short Bytes: Google has achieved the first successful SHA-1 collision attack. By creating a specially crafted PDF prefix, the researchers were able to generate 2 documents with the same SHA-1 digest. Using its cloud infrastructure, Google was able to compute the mammoth collision. After this, Google expects that the usage of the vulnerable SHA-1 encryption hash function will be depreciated.
After two years of hard work and research, Google has successfully broken SHA-1 encryption. The security researchers have been able to achieve the first real-world collision attack against this popular hashing function. Before going into the details of the demise of this building block of web encryption, let’s tell you a little about SHA-1 Encryption.What is SHA-1? What does it do?
SHA-1 Encryption stands for Secure Hash Algorithm. A hash is a unique code that’s based on some data input. When a person creates a password, it’s “hashed” and stored by the server. When you type a password, it’s hashed again and matched with original hash. In simpler language, SHA-1 generates a digital fingerprint of a file that allows one to verify the integrity of the file securely. If the hash function works properly, unique hashes will be produced.
SHA-1 Encryption was developed long ago by the NSA and it became one of the most important parts of many techniques used to encrypt the transmissions on the internet.
If SHA-1 is so useful, why did Google break it?
You’ve been asking this question ever since you read the headline, I know.
The real reason behind this deathblow is that the usage of SHA-1 is declining with time and it’s supposed to be deprecated. SHA-1 has been known to be vulnerable to theoretical attacks since a decade. Despite these issues, the algorithm is still used in many areas.
In its blog post, Google says that its finding emphasizes the need to sunset SHA-1 usage. The company has urged the tech industry to drop the usage of SHA-1 for many years. Back in 2014, the Chrome team announced that it’ll be dropping the use of SHA-1 Encryption.
What did Google actually do? What is a cryptographic hash collision?
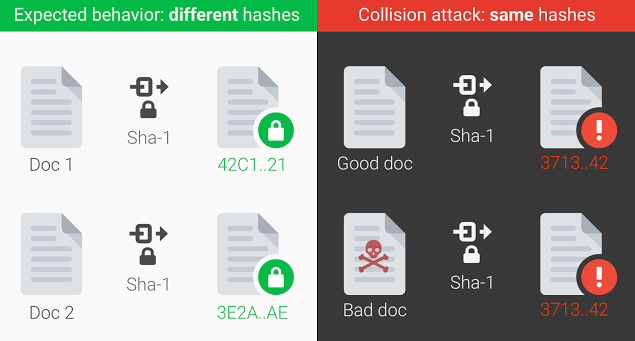
A cryptographic collision occurs when a hashing function breaks and two files end up having the same hash. It’s a very dangerous situation that can be exploited by the hackers to deceive systems that use hashes, and fool them into accepting a malicious file.
To achieve this collision, Google created a PDF prefix to let them create 2 documents with distinct elements, but with the same SHA-1 digest. Google used its cloud infrastructure to compute the collision, which is also one of the largest computations ever completed.
Wondering how huge was the computation? Let’s take a look at some numbers:
- Nine quintillion (9,223,372,036,854,775,808) SHA1 computations
- 6,500 years of CPU computation to complete the attack 1st phase
- 110 years of GPU computation to complete the 2nd phase
Having said that, we believe that security practitioners will soon switch over to more secure hashes like SHA-256 and SHA-3. Google will be disclosing the code after 90 days that will let anybody create a PDF pair with the same SHA-1 digest.

To showcase the attack, which is being called SHAttered, Google has also created a dedicated website. For more information, feel free to read this research paper. Here, you can read what Linus Torvalds has to say about this.
Also Read: DeepCoder: Microsoft’s New AI Writes Code For People Who Don’t Know Coding