Facebook Deletes ExtraTorrent Official Page And Disables User Accounts
Short Bytes: Facebook has removed the official page of ExtraTorrent. The social network has taken this step…
Short Bytes: Facebook has removed the official page of ExtraTorrent. The social network has taken this step…

Short Bytes: At the Black Hat 2016 hacker conference in Las Vegas, the world saw a…
Short Bytes: A security researcher has claimed that the newly-introduced Linux subsystem in Windows 10 could prove…
Short Bytes: In order to oppose the advent of mass surveillance programs in the UK, an…
Short Bytes: 10 members of China’s largest hacking group WooYun, including its founder Fang Xiaodun, were arrested last…
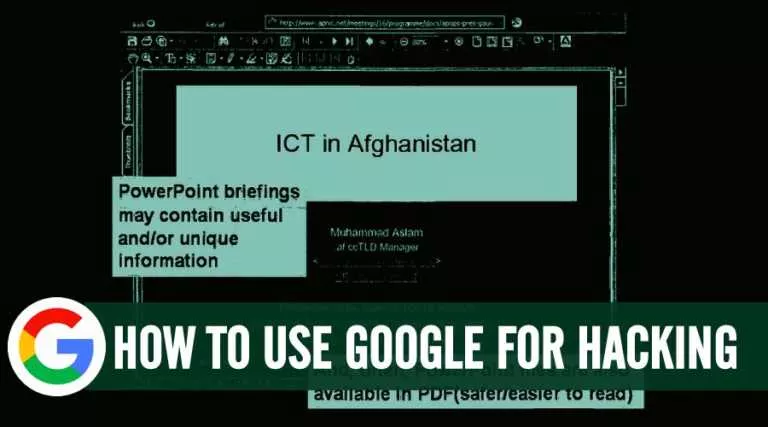
Short Bytes: Google Hacking is the method to access information that’s publicly available, but not intended…
Short Bytes: The Motion Pictures Association of America (MPAA) has taken serious measures to get rid…
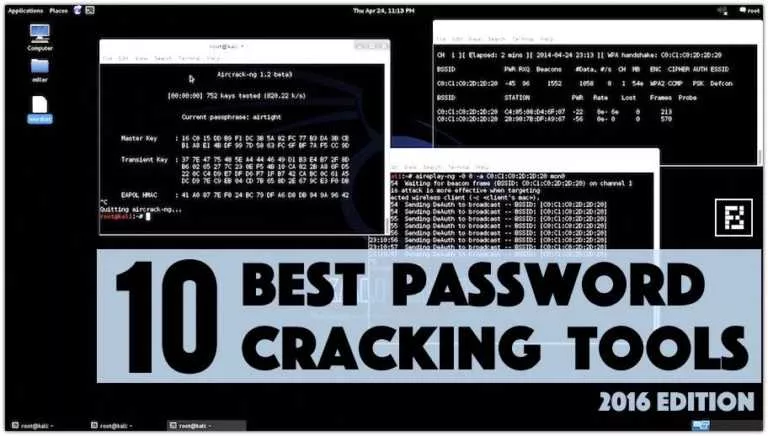
Password cracking is an integral part of digital forensics and pentesting. Keeping that in mind, we…

Short Bytes: Speaking at a press conference on Wednesday, the Republican presidential candidate Donald Trump urged…

Short Bytes: After the demise of KickassTorrents, internet pirates are looking for alternatives. The majority of…