Why Does 64-Bit Windows Need Two Program Files Folders — Program Files & Program Files (x86)
Short Bytes: Ever wondered why 64-bit Windows needs to have two Program Files folders? This is…

Short Bytes: Ever wondered why 64-bit Windows needs to have two Program Files folders? This is…
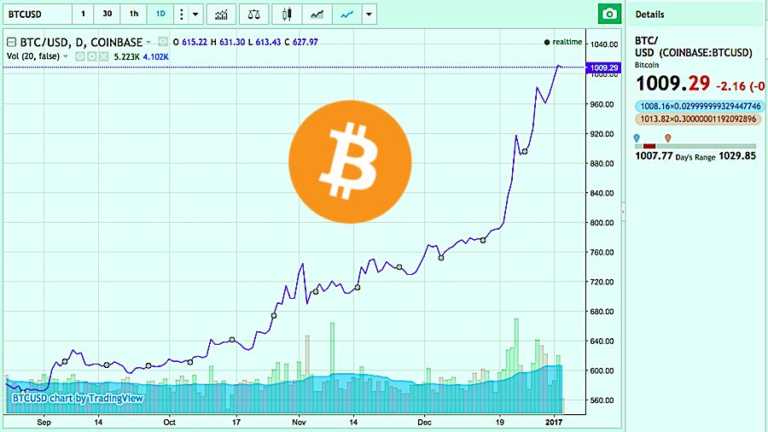
Short Bytes: The web-based cryptocurrency Bitcoin is basking in golden glory in the year 2017. For the first…

Short Bytes: The year 2017 has arrived. So, this year, are you ready to learn a…

Short Bytes: “Donald Trump hates computers” — this fact was once again confirmed recently. Talking to the…

Short Bytes: Twitter user WalkingCat has spotted a Game Mode in Windows 10 Build 14997. As…

Short Bytes: There are many different operating systems around and they have their weaknesses. There’s a long-standing…

Short Bytes: Earlier this month, a new set of minimum security requirements for Certificate Authorities was…

Short Bytes: In a recent interview, Microsoft’s Chief Marketing Officer, Chris Capossela, agreed that the forced Windows…
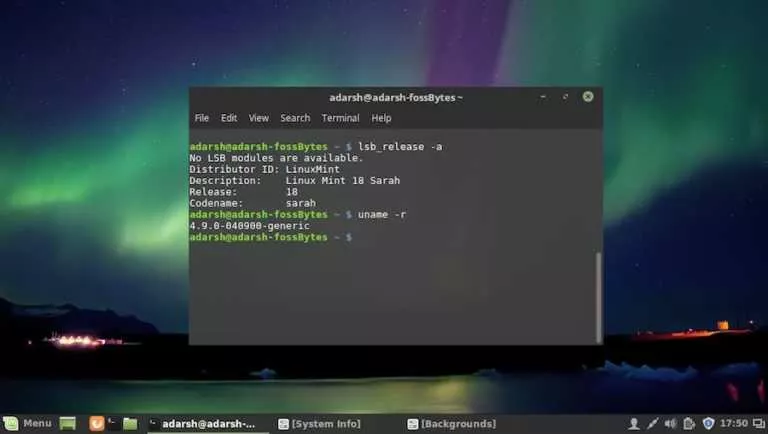
Short Bytes: Linux kernel 4.9 was released on December 11, and it brought along numerous hardware…

Short Bytes: Nokia has filed several lawsuits aimed at Apple. The company claims that the iPhone…