Here’s How Your Sleeping Mac Can Be Hacked In 30 Seconds

Short Bytes: A security researcher has exploited a flaw in macOS and used his $300 device and open source software to hack a sleeping Mac. The loophole is related to Mac’s way of storing passwords in memory. Apple has released a patch in macOS 10.11.12 update, and the users are advised to grab it.
Last month, we told you how the Chinese security researchers were able to crack the security of Windows 10 browser, Adobe Flash, Safari, etc. in few seconds. This was followed by another news in December that was about credit/debit card hack in 6 seconds.Continuing this “hacked in seconds” tradition, I’m here to tell you how hackers can get their hands on your Mac in just 30 seconds. This technique has been devised by Ulf Frisk, a Swedish pen-tester and hacker.
In his blog post, Frisk explains that the hardware used to hack a Mac costs $300 to build. This hacking device can be connected to a Mac via Thunderbolt port.

The root cause of the hacking vector is Mac’s habit of storing the password in memory in clear text. When the computer enters sleep mode, the password resides there. During the rebooting process, there’s a window of few seconds before the memory is overwritten with new content.
An attacker just needs to connect the hacking device (connected to another laptop) to Mac’s Thunderbolt port and force a reboot.
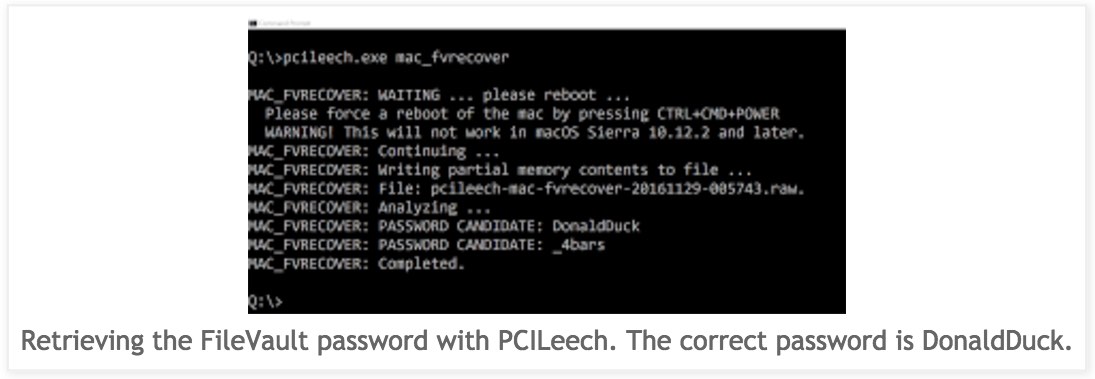
Frisk has also shared a video that shows what an attacker would need to do. Apart from the hardware, one would also need Frisk’s open source PCILeech software. For more technical details, you can read his blog post.
Apple has patched this security loophole in macOS 10.12.2. So, you’re advised to grab the update and secure your Mac.
Did you find this article on Mac bug interesting? Don’t forget to share your views in the comments below.
Also Read: Most Ubuntu Linux Installations Are Affected By A Dangerous Remote Code Execution Bug