This Nearly “Impossible to Trace” Spyware is Used by 32 Governments to Spy on You
 Short Bytes: In 2015, the infamous spyware FinFisher is spread in 32 countries to perform advanced citizen surveillance. Citizen Lab, a security watchdog, has uncovered the nearly untraceable IP addresses and servers of the spyware. Read more and find out how it works and if it’s used by your government.
Short Bytes: In 2015, the infamous spyware FinFisher is spread in 32 countries to perform advanced citizen surveillance. Citizen Lab, a security watchdog, has uncovered the nearly untraceable IP addresses and servers of the spyware. Read more and find out how it works and if it’s used by your government.
The preying eyes of your government are more active than ever and it’s using more advanced tools for surveillance purposes. Recently in the data breach at the Hacking Team, it was revealed that multiple governments contacted them to obtain spyware tools.
One such famous product in the spyware market is FinFisher, also known as FinSpy. This surveillance software came into the limelight in 2014, when a hacking attack at its marketing company Gamma International exposed it to the world.
One year after the hack, this sophisticated computer software suite, sold exclusively to governments and law enforcement agencies, is alive and serving more customers than ever. This suite is used to target computers or phones, and monitor all activities including calls, emails and messages.
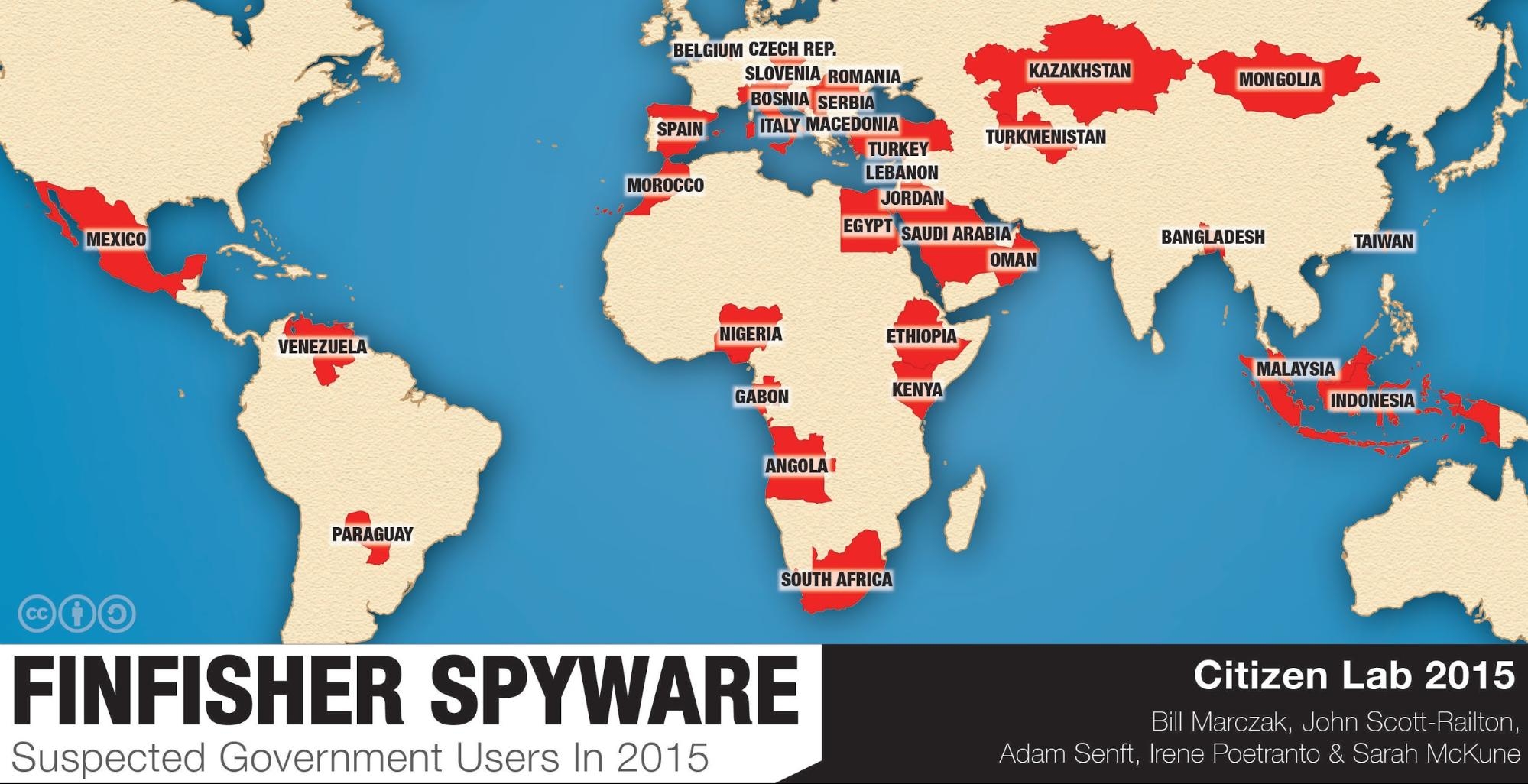
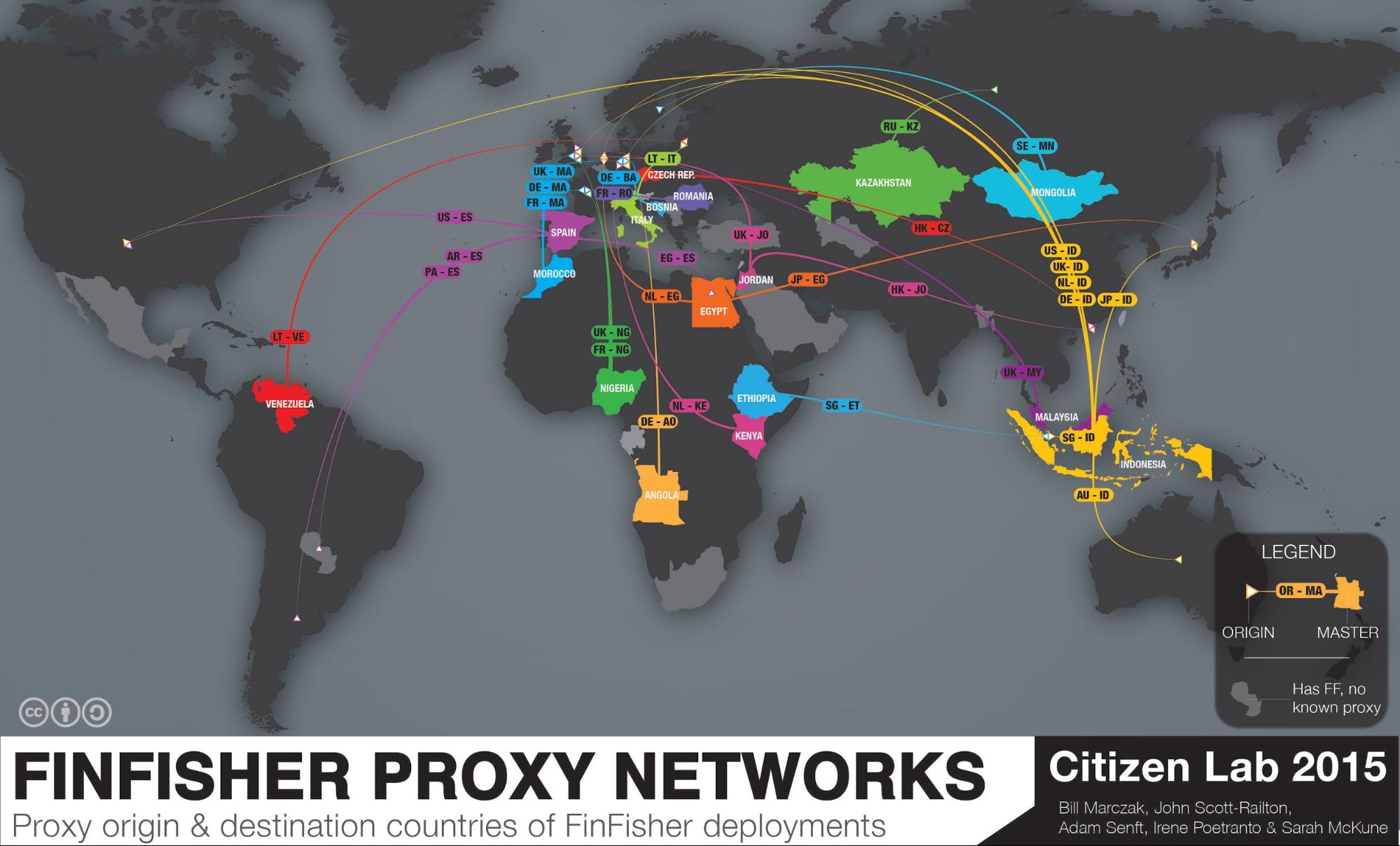
Citizen Lab, a security watchdog, has published a new report unmasking the true locations of the master servers to identify the governments using FinFisher. The firm scanned the internet for FinFisher servers and separated masters from proxies and located 32 governments and 10 entities that are directly related to FinFisher.
The lab has been able to identify these servers that are claimed to be practically impossible to trace by the spyware makers.
Governments using FinFisher include those of Mongolia, Kazakhstan, South Africa, Oman, Bangladesh, Ethiopia, Taiwan, Malaysia, Nigeria, Mexico, Spain, Venezuela and other. Many suspected governments using FinFisher spyware have past records of human rights violations.
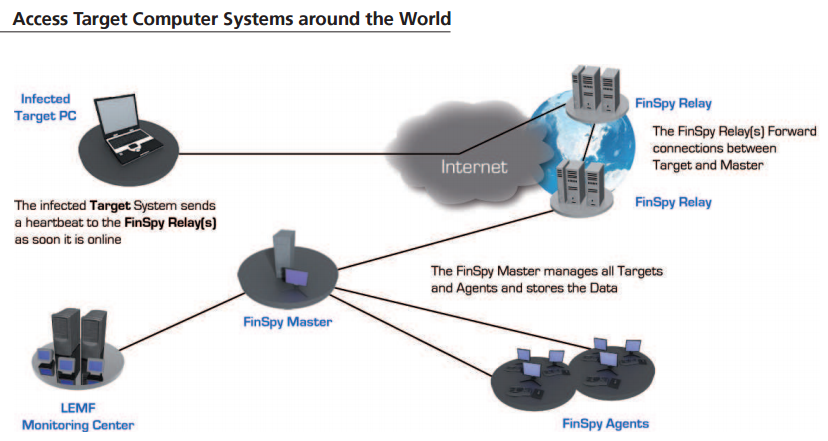
Citizen Lab researchers write than each instance of FinFisher includes the address of a command and control server that the spyware reports back to.
“These C&C servers are typically FinSpy Relays, which forward connections back and forth between a device infected with FinFisher, and a FinSpy Master. The purpose of the FinSpy Relay is explicitly to make it “practically impossible” (their emphasis) for a researcher to discover “the location and country of the Headquarter,” Citizen Lab writes.
The researchers were able to find some connection between Hacking Team and FinFisher IP addresses. Instead of being competitors, both of them shared some common clients.
They collected a total of 135 IP addresses belonging to FinFisher boxes, but not all of them were pointing back to one specific country. “So there’s definitely more customers,” one of the researchers Marczak told Motherboard.
“In presenting our scan results, we do not wish to disrupt or interfere with legitimately sanctioned investigations or other activities. Instead, we hope to ensure that citizens have the opportunity to hold their governments transparent and accountable,” writes Citizen Lab in its report.
Read the complete report here for the list of IP addresses and more insights.
Also read: “You Can Hack a Computer Just by Looking at It” – HP Explains Visual Hacking
[adinserter block=”12″][adinserter block=”13″]