7 Malicious Chrome Extensions Infected 100,000+ Users, Mined $1000 Cryptocoins
We have seen many examples where malicious chrome extensions are used to target users and steal their information. Last month, the Facexworm malware campaign was reported by TrendMicro whose working was similar to Digimine.
Now, the security firm Radware has disclosed a group of 7 Chrome extensions hiding the malware Nigelthorn that were living on the official Chrome store.
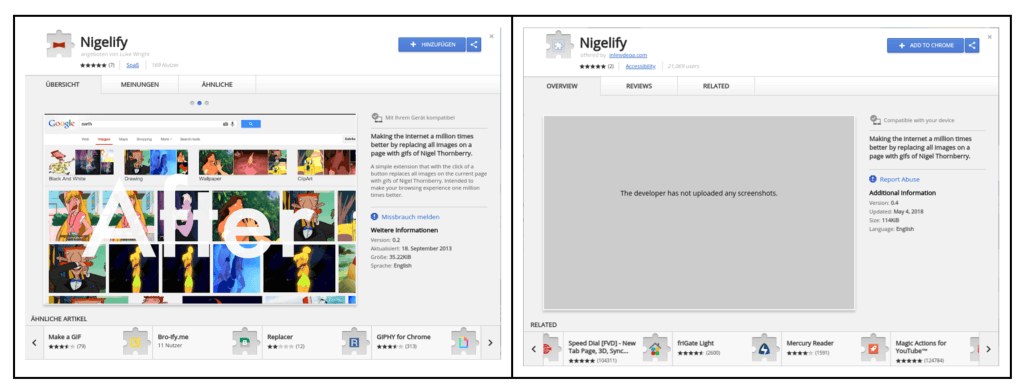
The zero-day malware is named so because the security firm found it masquerading as the extension Nigelify which replaces images with GIFs of Nigel Throneberry. Radware found its malicious copycat, responsible for a large portion of infections, at a global manufacturing firm which is their customer.
Nigelthorn is expected to have been active since March 2018 and infected more than 100,000 users in over 100 countries with 75% of them in Phillippines, Venezuela, and Ecuador.
The attackers behind the malware campaign created a total of 7 malicious copied versions of legitimate Chrome extensions including Nigelify, PwnerLike, Alt-j, Fix-case, Divinity 2 Original Sin: Wiki Skill Popup, keeprivate, and iHabno.
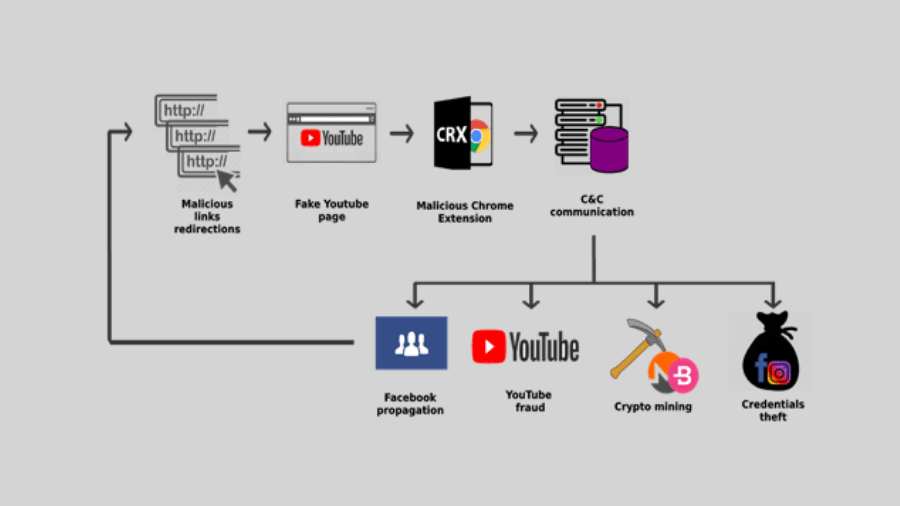
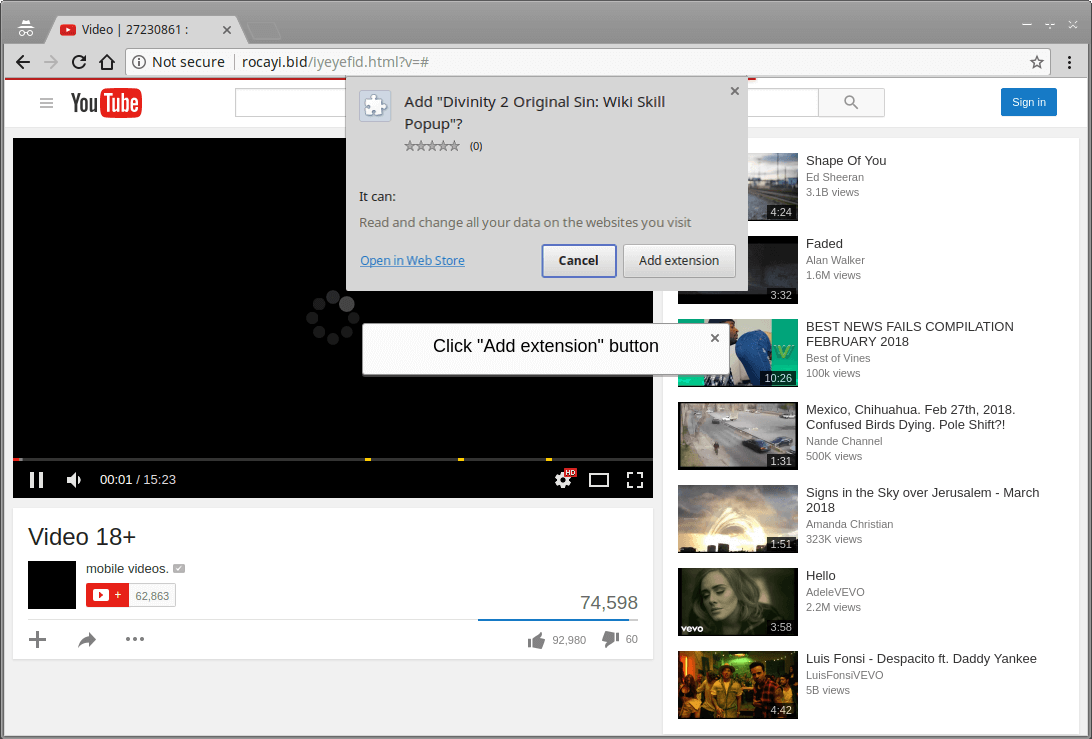
The malware campaign works similar to Facexworm. A Facebook user clicks a socially engineered link, lands on fake YouTube page, downloads a malicious Chrome extension.
After ending up on user’s device, the extension contacts the C&C server to download the payload. It can perform different activities like stealing Facebook credentials and Instagram cookies, YouTube fraud, and propagating further on Facebook through victim’s friends.
It also installs cryptocurrency mining scripts to mine Monero, Bytecoin, and Electronuem. Radware says (at the time of writing the blog post) around $1000 worth crypto coins were mined in last six days, monthly in Monero.
One important thing about Nigelthorn is that it affects both Windows and Linux users. But it’s confined to the Chrome browser. Radware believes that people who don’t use Chrome browser are not at risk.
When it comes to persistence, Nigelthorn can close the extensions tab when the user tries to remove the malicious extension. Also, it tries to prevent people from accessing potential Facebook and Chrome cleanup tools.
The extensions were reported to Google and now removed from Chrome Store. It’s only a matter of time when such malware might return, given the success attackers have acquired in uploading malicious extensions on the Chrome store in recent times.
Also Read: Just 12% People Want To Pay For Facebook If Their Data Isn’t Collected And Sold