37 Million Adulterers Exposed, Online “Cheating” Site Ashley Madison Hacked

Online cheating website AshleyMadison.com has been hacked, and as a result, large chunks of data has been stolen. The compromised data has been posted online by some group or individual that claims to hack the user database and financial records of the company. According to the reports, the Ashley Madison hack has risked the personal information of about 37 million adulterers.
ALM CEO Noel Biderman has confirmed the Ashley Madison hack in a conversation with the security firm KrebsOnSecurity. He said that his engineers are working day and night to recover the leaked data.
Biderman said: “We’re not denying this happened. Like us or not, this is still a criminal act.” In the past, Biderman’s company has claimed that Ashley Madison is world’s second most popular dating site.
Apart from the snippets of private user data of about 37 million users, the Ashley Madison hackers leaked employee information, internal server maps and company’s financial data. It should be noted that just two months ago, hackers stole online user data from AdultFriendFinder.com.
Also Read: NSA Hacked Kaspersky Labs and Other Anti-virus Software to Track Users
Along with the data from Ashley Madison hack, The Impact Team has tried to justify its actions by calling it a response to an ALM service that promises to completely erase user profiles in $19. The Impact Team calls these claims false as the real names and addresses aren’t erased.
Here’s a snippet with message:
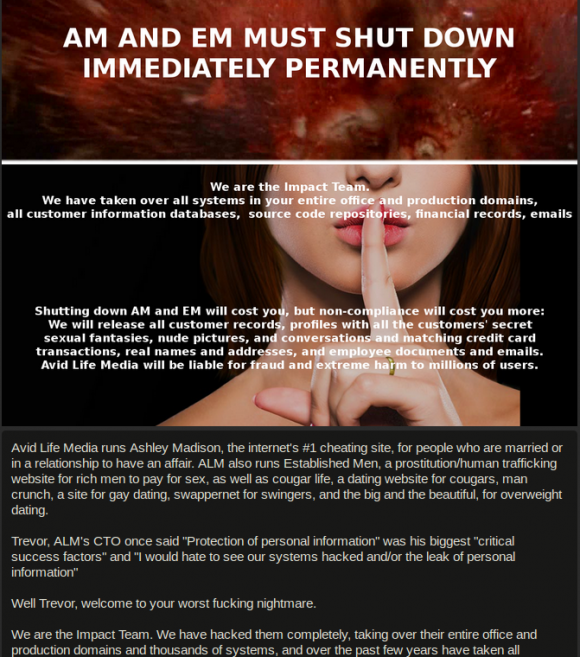
In response to Ashley Madison Hack, ALM said that it’s an authorized attempt to gain control over the systems and any parties responsible for the act will be held responsible.
Having anything else to add to the story? Tell us in comments below.
Subscribe to fossBytes newsletter for more updates and security news.[newsletter_signup_form id=1]