500,000 Windows Users Infected By 15-Year-Old Stantinko Malware

Short Bytes: The security researchers have found a malware that uses stealthy techniques to perform monetization by injecting ads. Called Stantinko, this malware also has the power to install additional modules to gain complete administrative control. Stantinko installs two malicious extensions, which seem to be legitimate, for performing advertising fraud.
The security researchers at ESET have uncovered a stealth malware named Stantinko. When the researchers started analyzing this malware, they were pretty confused with little idea if it was an adware or spyware.The researchers have traced Stantinko malware since 2002. Since then, the malware creators have tracked its activity and increased sophistication. The malware is still active with the new version of the main services which was released earlier this year.
Some of the key points that you must know about Stantinko malware are:
- The chief targets of Stantinko malware are Russia and Ukraine, with 46% and 33%, respectively.
- The botnet is primarily an adware that installs browser extensions for injecting ads during web browsing.
- Components of the malware are hidden inside legitimate FOSS software.
- It installs multiple persistent services to resist the cleaning attempts.
What sets Stantinko adware apart from others is its ability to download and execute other payloads. The researchers were able to find additional modules deployed by the adware, including fully-featured remote control backdoor, a Google searching bot, and a WordPress and Joomla brute forcing tool.
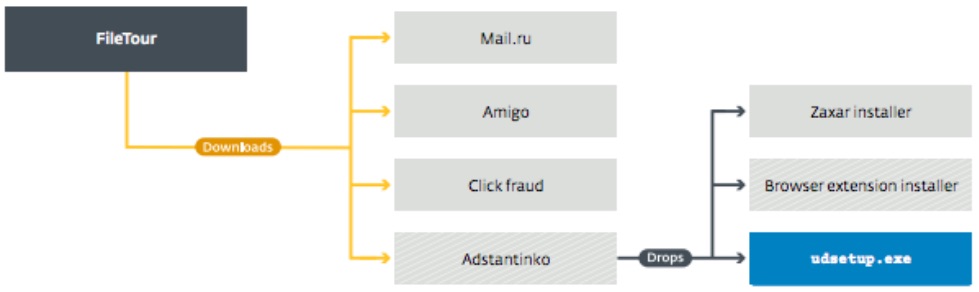
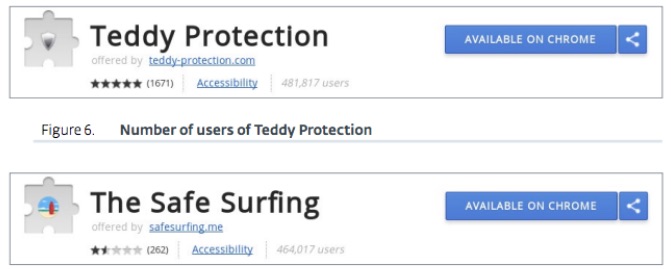
The current version of the malware is distributed via torrent. The initial infection file, FileTour, is a downloader that installs multiple malicious applications. Stantinko’s persistent services also install malicious extensions, which seem legitimate, for performing advertising fraud. The two installed extensions are The Safe Surfing and Teddy Protection, whose combined installations are around 500,000.
Have something to add to this story? Don’t forget to share your views.
Source: ESET, Bleeping Computer
Also Read: 5 New CIA Malware Unveiled By WikiLeaks — HTTPBrowser, NfLog, Regin, HammerLoss, Gamker