Hacker Hacked IoT Devices For 8 Years Just To Download Free Anime

A hacker operated a network of botnets and exploited vulnerable D-Link Network Attached Storage (NAS) and Network Video Recorders (NVR) devices for 8 years, ZDNet reports. The reason: he wanted to watch Anime for free. He only targeted NAS and NVR IoT devices and didn’t attack any other device.
The botnet dubbed Cereals started operating in 2012 and by 2015, it had more than 10,000 bots connected to online websites for downloading anime videos.
Interestingly, researchers named the botnet “Cereals” after its subnet’s naming convention.
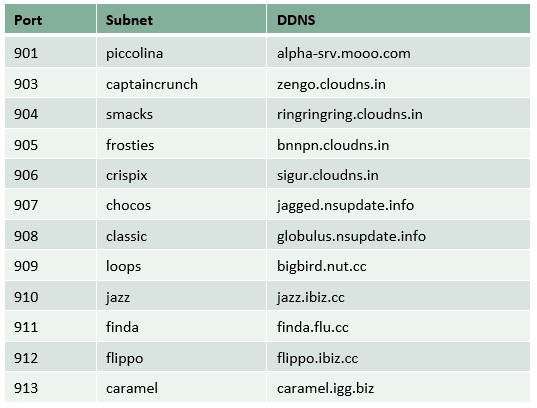
Cybersecurity company Forcepoint has published a report detailing the working of Cereals botnet. The report mentions that Cereals botnet did its dirty work by exploiting a single vulnerability in NAS and NVR devices throughout 8 years.
The hacker scanned the internet for exploitable NVR and NAS devices and then used the botnet to harvest data. The botnet exploited a flaw in the SMS notification feature of the target devices. It allowed the botnet operator to send an HTTP request to a device’s built-in server and execute commands with root privileges.
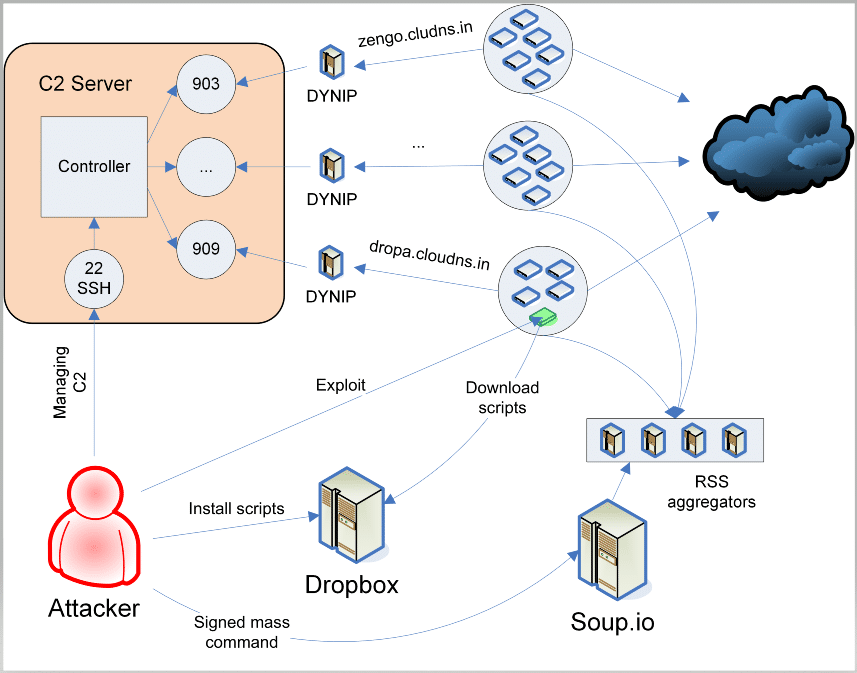
Source: ForcepointAccording to the researchers, despite exploiting a single vulnerability for over 8 years, the Cereals botnet deployed advanced mechanisms to attack devices. It has been discovered that the botnet deployed at least 4 backdoor mechanisms to infect devices.
Surprisingly, the hacker patched the infected systems so as to prevent other hackers from compromising the system.
However, the botnet never faltered from his primary objective of downloading Anime videos for free and never attempted DDoS attacks or tried to access user data. This shows that the operator had no criminal intentions.
Cereals botnet has faded over time, majorly due to two factors:
- The D-Link NAS and NVR devices targeted by him over the years have been abandoned by the owners.
- Ransomware named Cr1ptT0r removed the Cereals botnet from the majority of devices in 2019
Several security researchers fear that Facepoint’s research might attract other malware operators to target the vulnerable devices and they might have criminal intentions.