Emotet Malware Shut Down Microsoft’s Entire Network By Overheating PCs

Emotet is one of the notorious malware wreaking havoc across industries by hacking systems. In that latest attack, it took down an entire network of Microsoft by overheating computers.
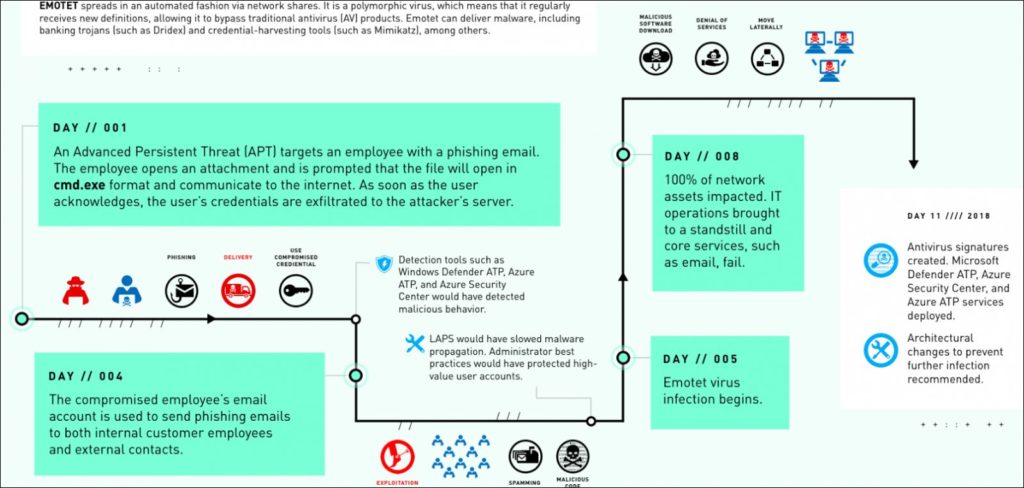
According to a report by Microsoft Detection and Response Team (DART), Emotet tricked one Microsoft employee into opening a malicious email attachment. A series of events that followed led to a week-long shut down of the organization’s core services by maxing out CPUs.
How was the attack executed?
Emotet malware managed to evade all detection systems as it is regularly controlled by the attacker’s command and control (C2C) server.
Five days after the employee’s credentials were extracted by the phishing email attachment, the Emotet payload was delivered and executed on Fabrikam’s (an alias used for the victim by Microsoft in its case study) PCs.
Soon, malware actors started targeting more employees of Fabrikam and their external contacts using stolen credentials and more systems were affected. The malware took over the control of the entire network by gaining access to the admin account.
Within 8 days since the email attachment was first opened, the entire network crashed despite the best efforts from the IT department of the entity.
All the PCs connected to the network started experiencing overheating, freezing, abrupt shutdowns and reboot due to Blue Screen of Death. Emotet malware also chugged all the bandwidth thus slowing down the internet connection of the network.
DART’s case study mentions: “When the last of their machines overheated, Fabrikam knew the problem had officially spun out of control. We want to stop this hemorrhaging.”
The entire network was brought down to its knees including the 185-surveillance camera network due to Emotet malware.
“Emotet consumed the network’s bandwidth until using it for anything became practically impossible. Even emails couldn’t wriggle through,” reads the report.
Containment Efforts
8 days after the first system froze, Microsoft’s cybersecurity team DART was called to Fabrikam. They controlled the malware attack by using buffer zones that isolated assets with admin privileges. They also uploaded new antivirus signatures and installed Microsoft Defender ATP and Azure ATP to get rid of the malware completely.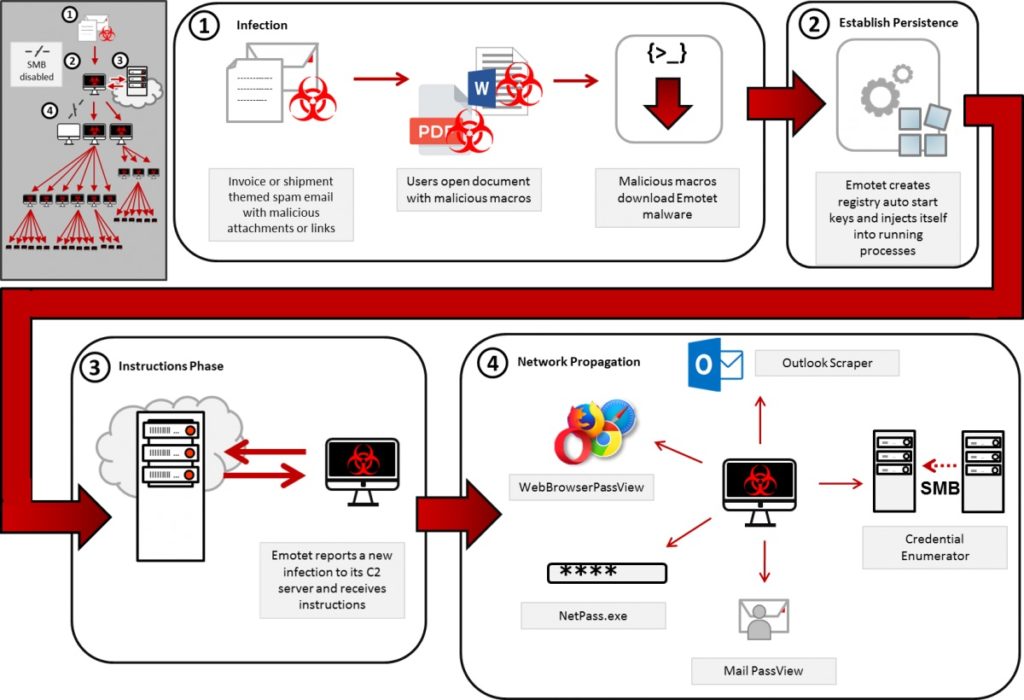
Since Emotet paralyzed their own network, Microsoft recommends users to deploy email filtering tools to avoid potential phishing attacks and multi-factor authorization to evade illegal access to the system.






