‘Dragonblood’ Flaw In WPA3 Lets Hackers Easily Grab Your Wi-Fi Passwords

In late 2017, KRACK Attack crippled the popular 13-year-old WPA2 Wi-Fi standard used in our homes, offices, and public networks. The flaw allowed hackers to gain access to unencrypted traffic between the access point and the device — there were possibilities of breaking encryption as well.
Months later, the Wi-Fi Alliance released the WPA3 protocol to bring improved wireless security to users as well as to those who didn’t meet the minimum password security requirements. Now, it seems that even WPA3 isn’t completely secure due to some inherent design flaws. The newly found flaws can help an attacker to crack the passwords and further access the encrypted traffic exchange taking place among the devices.
In a research paper titled Dragonblood, published by security researchers Mathy Vanhoef and Eyal Ronen, it has been revealed that WPA3’s secure handshake called Simultaneous Authentication of Equals (SAE), commonly known as Dragonfly, is affected by password partitioning attacks.
For those who don’t know, such attacks are very much like the popular dictionary brute-forcing attacks coupled with the abuse of cache-based side channel leaks. “These allow an adversary to impersonate any user, and thereby access the Wi-Fi network, without knowing the user’s password,” the researchers wrote.
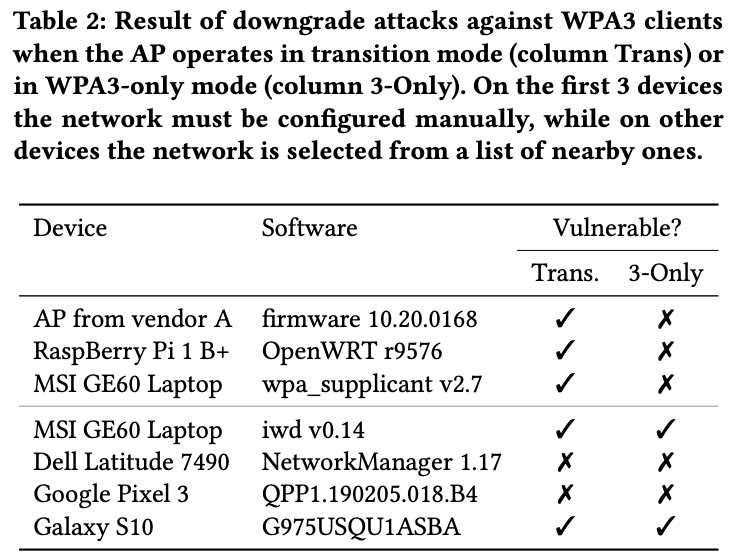
What makes this attack even more worrying is its cost-effectiveness and high efficiency. For example, to brute-force an 8-character lowercase password, one needs to spend less than $125 to run calculations in the cloud.
The researchers have made recommendations that WPA3 protocol doesn’t meet the standards when it comes to ensuring the security of our Wi-Fi networks and that it needs further improvement. However, they’ve called it an improvement over the WPA2 standard.
The researchers have also informed the Wi-Fi Alliance about these flaws, and they’ve worked closely with the organization to fix the issue. The patches for the same have been released, and they’ll be made available via the usual software updates on different devices. So, updating your devices and installing the latest patches is the only way to move forward.
Also Read: Your Android Phone Is Now A Physical Security Key — Here’s How To Use It