DDoS Attacks Are Now Stronger Than Ever, 12 Mega Attacks in Recent Times

Short Bytes: The infamous DDoS attacks have increased at a staggering pace in the recent past. According to a latest report, DDoS attacks have grown by 132 percent compared to this time last year. The internet has also witnessed 12 Mega Attacks in Q2 2015.
This program called Extreme DDoS Defense is something that is being inspired by the increasing number of DDoS attacks in recent times. DDoS attacks have become a greater threat in the second quarter of 2015, according to the latest State of the Internet report from Akamai.
Compared to this time last year, DDoS attacks have grown at an unprecedented pace of 132 percent. This increase is seven percent since the last quarter and the world has also seen 12 mega attacks that peaked at more than 1,000 Gbps and 50 million packets per second.
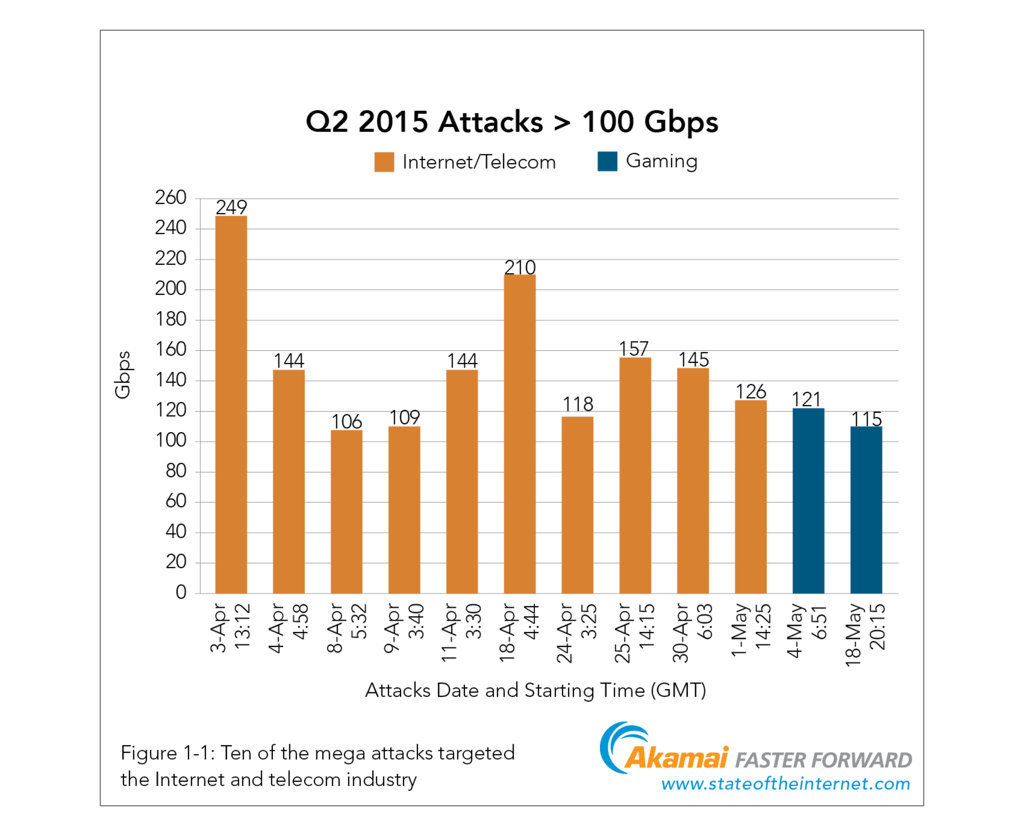
According the report, Mega attacks have become more common and very few organizations have the technology to defend themselves against such attacks. The largest DDoS attack was recorded last quarter that lasted for more than 13 hours and peaked at 240 Gbps.
To carry out such attacks, the unsecured home devices that connect using the Universal Plug and Play (UPnP) Protocol are largely used as SSPD reflectors. Also, the world’s most popular blogging platform and content management system, WordPress is a regular and attractive target for attackers and they exploit the vulnerabilities in the third party plugins and themes.
“The threat posed by distributed denial of service (DDoS) and web application attacks continues to grow each quarter,” said John Summers, vice president of Akamai’s cloud security business unit. “Malicious actors are continually changing the game by switching tactics, seeking out new vulnerabilities and even bringing back old techniques that were considered outdated.”
According to Akamai’s, DDoS attacks have become the most commonly used method by the attackers to target an organization’s security, and cyber-criminals are deploying new tactics by seeking out new vulnerabilities.
Also read: IBM: Hackers are Using Tor Network More Frequently For Launching Hacking Attacks
Having something to add? Tell us in the comments below.
[adinserter block=”12″][adinserter block=”13″]