This Code On USB Can Trigger BSOD Even On Locked Windows PCs
In the past, we’ve told you about the perils of picking any random USB drive and using it. It might contain malware and dangerous scripts to target your online accounts. A Bitdefender security researcher, Marius Tivadar, has underlined the importance of this issue with his proof-of-concept code (Via: CSO Online).
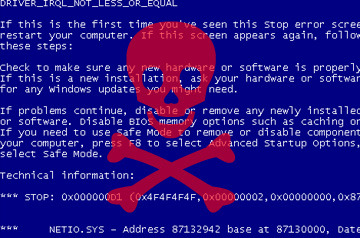
When put on a USB stick, this malicious code can trigger the infamous Blue Screen Of Death (BSOD) on Microsoft’s Windows operating systems. The flaw being exploited here deals with how Windows handles NTFS images.
On the project’s GitHub page, Tivadar describes one can generate BSOD using a “handcrafted NTFS image.” Further, this denial of service can be triggered from admin, limited user account, or user mode. “It can even crash the system if it is in locked state.” Watch the attack in action here.
The affected Windows versions (but not limited to) that can become a target of this attack are:
- Windows 7 Enterprise 6.1.7601 SP1, Build 7601 x64
- Windows 10 Pro 10.0.15063, Build 15063 x64
- Windows 10 Enterprise Evaluation Insider Preview 10.0.16215, Build 16215 x64
The documentation on GitHub also describes the method of preparation of the NTFS image. After the attack, the auto-play is activated and the system gets automatically crashed.
As auto-play takes action even when the system is locked, so this attack works in this case as well. Tivadar believes that this kind of behavior should be discouraged.
He further notified Microsoft about the issue but the company didn’t assign a CVE or issued a formal fix. However, the company has fixed the issue at some point of time without informing Tivadar. As a result, BSOD code attack doesn’t work on the recent Windows 10 Build 16299.
Did you have something to add to this story? Should Microsoft change the way auto-play operates? Share your views in the comments section and keep reading Fossbytes.
Also Read: “Fake Zuckerbergs” Are Tricking Facebook Users Into Sending Money