Here’s How You Can Check Pegasus Spyware Using MVT?

There’s a lot of hue and cry regarding user privacy in the media right now. The credit goes to the Israeli spyware Pegasus, allegedly used by several governments to snoop on their critics.
A recent leak covered by The Pegasus Project — a consortium of non-profit organizations and various journalists — claimed to have 50K phone numbers that likely belong to users who might be victims of the Pegasus spyware.
Since the leak, several developments of the story have followed. The latest development, reported by TechCrunch, mentions a tool that can detect Pegasus on Android and iOS. The toolkit, which was shared by Amnesty International’s research team, is called the “Mobile Verification Toolkit (MVT).”
Unsurprisingly, the same toolkit was used by Amnesty, one of the forces behind The Pegasus Project, to run forensic scans on the devices whose phone numbers were mentioned in the leak. The MVT results successfully detected Pegasus attacks carried out on those devices.
Moreover, the organization also remarked that it was easier to detect the spyware on iOS than Android because it had more forensic traces.
How Does MVT Detect Pegasus?
To trace one of the world’s most sophisticated spyware programs, MVT relies on running forensic scans that look for “Indicators Of Compromise” or IOCs. These IOCs are basically signs that are believed to exist on every Pegasus-infected device.
An example of an IOC could be a domain address used by Pegasus’s creator, the NSO Group, in its operations. In infected phones, this domain name might reside inside an SMS or an e-mail.
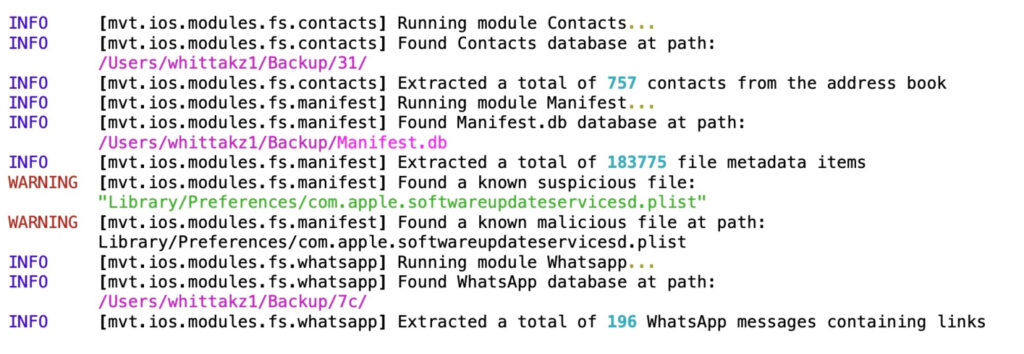
Before looking for signs of a Pegasus threat, the MVT lets you create a backup of your device data. You will then have to feed in Amnesty’s latest IOCs to the toolkit. The toolkit will run scans against the IOC data and highlight any suspicious presence in the output folder. According to TechCrunch, the scanning process takes about 1-2 minutes to complete.
How Can I Use MVT To Scan For Pegasus?
Since MVT is open-source, you can easily download it from its GitHub page. Once that’s done, you can head out to this website and follow the given instructions for installation. However, MVT does not have a user-friendly interface, so you’ll need to have some command line know-how before you begin.
Moreover, before the scan can start, you’ll have to feed in the latest IOC uploaded by Amnesty’s researchers from this page. Make sure you use the latest IOCs to maximize the accuracy of the scan.
The IOCs are constantly being improved to remove false detections and increase the effectiveness of MVT. Because of this, there is a chance the toolkit might flag your device as infected even when it’s not.
For most people, minus journalists, the risk of having Pegasus on their phone is relatively low. But, if you still want to be totally sure and know your way around the command line, it won’t hurt to run an MVT scan.
For the layman, I’d suggest you wait for someone to create a user-friendly version of MVT — I’m pretty sure developers are working on one as I’m writing this.