Edward Snowden Gets Bombarded With 47GB of Twitter Notifications
Short Bytes: Former NSA contractor and a newbie to Twitter, Edward Snowden, forgot to turn off…
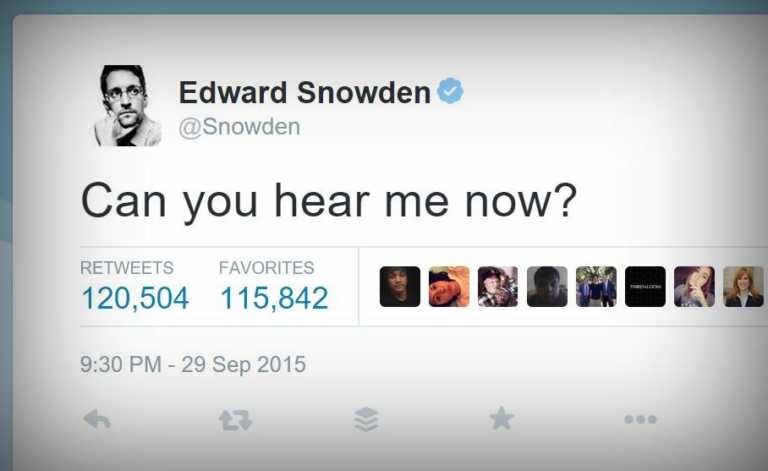
Short Bytes: Former NSA contractor and a newbie to Twitter, Edward Snowden, forgot to turn off…

Short Bytes: The humble wireless router in your home, as you might not think, could be…

Short Bytes: As more and more Linux systems are going online, the threat to the once-secure…

Short Bytes: To address your privacy concerns, Silent Circle has tried to create the super-secure Android…

Short Bytes: Security firm Zerodium has launched “The Million Dollar iOS 9 Bug Bounty”, that offers…
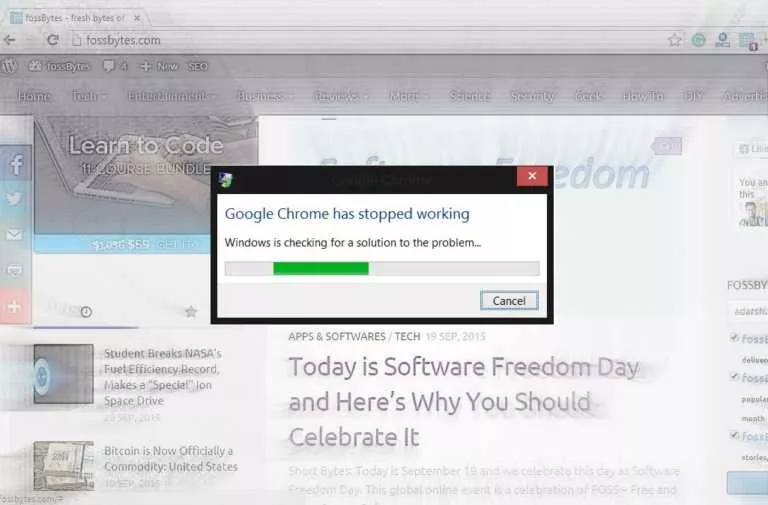
Short Bytes: Do you want to crash someone’s Google Chrome just for the heck of it?…

Short Bytes: Do you have a feeling that NSA and its British counterpart GCHQ spied on…

Short Bytes: PARC has developed a self-destructing computer chip under DARPA’s vanishing programmable resource project. The…

Short Bytes: MIT may boast of having one of the smartest bunch of people under one…

Short Bytes: A recent report from the Privacy International reveals a fake baby car sear that…