Highrise: How This CIA Malware Spies And Steals User Data Using SMS

Short Bytes: The latest WikiLeaks Vault 7 leak deals with an Android malware that doesn’t need the internet to talk to the CIA servers and spy on the users. Named Highrise, this malware acts as an SMS proxy to send stolen data. Highrise works on Android version 4.0-4.3; it’s installed under the name TideCheck.
Last week, we wrote about the CIA’s implants BothanSpy and Gyrfalcon, which stole SSH credentials from Windows and Linux machines. The next addition to these ongoing WikiLeaks Vault 7 leaks is an Android malware named Highrise.What sets Highrise apart from most of the previously leaked tools is its ability to steal data from a user’s smartphone and transmit it to the CIA host without the need of the internet. The Highrise malware does this by the means of SMS proxy.
What is Highrise malware? What are its capabilities?
According to the user guide leaked by WikiLeaks, the version 2.0 release of Highrise malware took place on Dec. 16th, 2013, and it was ported to Android 4.0-4.3, i.e., Android Ice Cream Sandwich and Jelly Bean. If CIA is still using this tool to spy on suspects, it will make perfect sense for them to have ported Highrise to newer versions.
The brief overview of Highrise Android malware calls it an Android application which is designed for mobile devices and acts as a redirector function for SMS. Precisely, Highrise is an SMS proxy that allows CIA to listen to the targets by maintaining a greater separation.
Also Read: CopyCat Malware Infects 14 Million Android Smartphones, Steals Sensitive Information
Some of the highlight features of Highrise malware are:
- Proxy “incoming” SMS messages received by HighRise host to an internet server
- Send “outgoing” SMS messages via the route of HighRise host
- Establish a channel between the HighRise field operator and server
- TLS/SSL secure communications
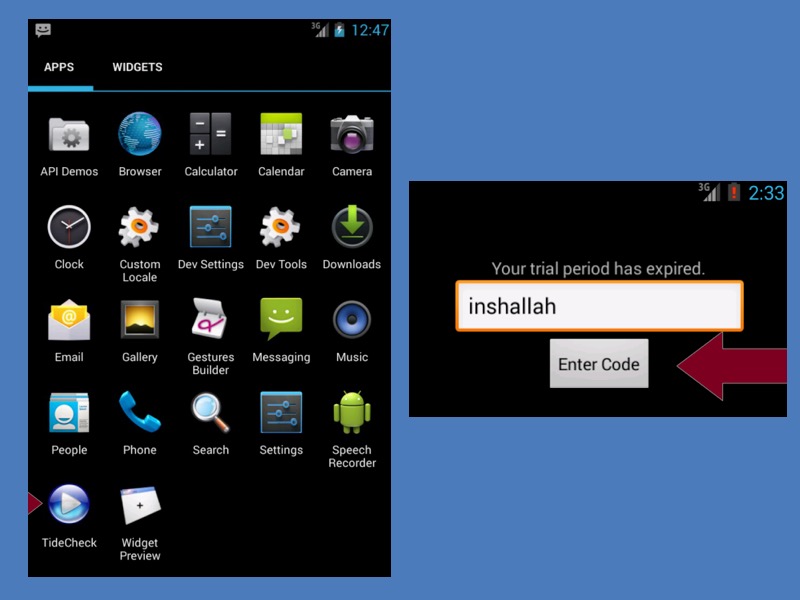
The manual for v2.0 mentions that the newer versions of Android (Android 4.0 and newer) don’t allow applications to register the handset events immediately after the installation. So, the Highrise malware app must be manually run once.
In the list of apps, Highrise is listed as TideCheck app. To activate it manually, as mentioned above, one must tap on it to start and enter the password in the prompt. The password is ‘inshallah.’
After the configuration, Highrise can be used to send short messages from the Highrise host to the CIA server. It keeps running in the background and starts when a person’s phone is powered on.
Read our complete WikiLeaks Vault 7 coverage here.
Source: WikiLeaks — Highrise
Also Read: Don’t Use This “Fake TOR Browser” — Scammers Are Fooling People