Bad Rabbit Ransomware Attack Is On The Rise — Here’s What You Need To Know
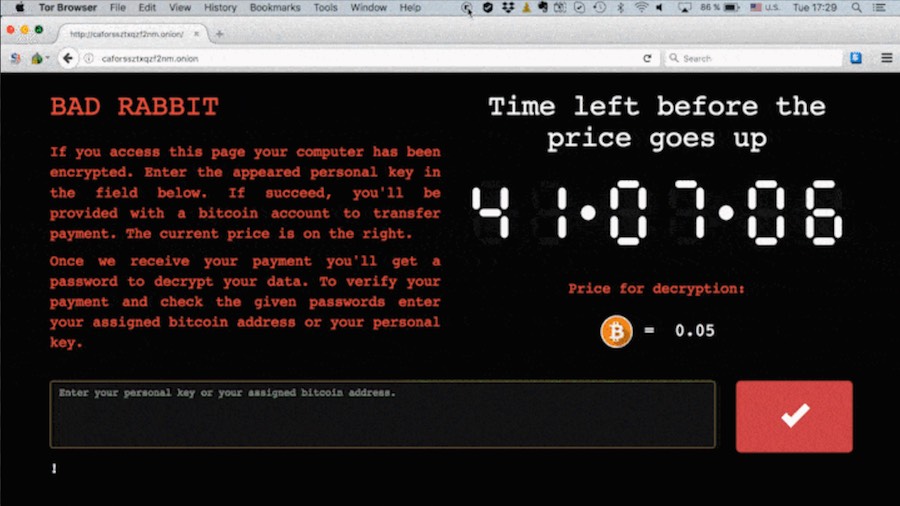
Victims of this ransomware are being redirected to a site on the darknet from legitimate news websites. Users are prompted to install the malware which is disguised as Adobe Flash player. Upon installation, all their files get encrypted, and the victim is asked for a payment of 0.05 Bitcoin ($276.85 at the time of publication) to gain access to the encrypted files. Kaspersky Lab has identified almost 200 targets in Turkey and Germany.
When the disguised program is installed, the malicious DLL is saved as C:\Windows\infpub.dat which, in turn, installs the malicious executable file. The spyware also installs a modified bootloader, so users lose complete access to their computer.
“What’s more, infpub.dat acts as a typical file-encrypting ransomware: it finds the victim’s data files using an embedded extension list and encrypts them using the criminal’s public RSA-2048 key,” said researchers at Kaspersky Lab.
A tweet by Group-IB shows a countdown timer displayed along with the message on-screen. Victims have around 40 hours to make payment, and once the timer overflows, the ransom will increase.
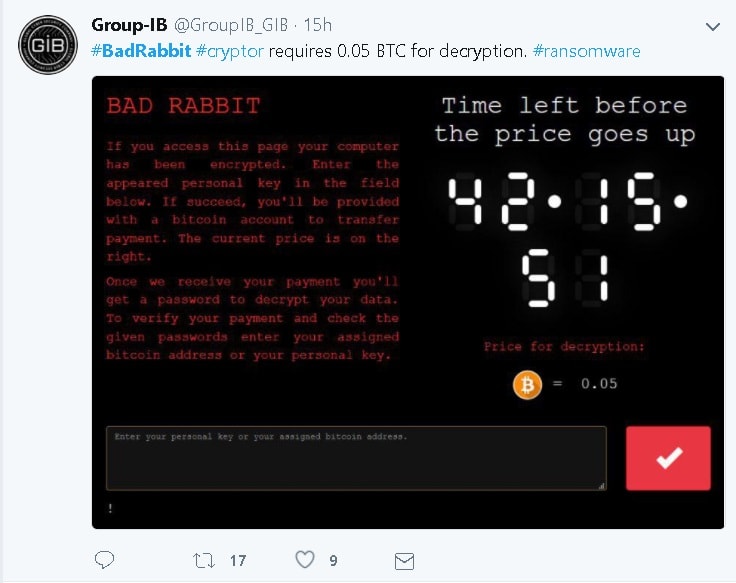
Interfax Ltd, a major news company in Russia, tweeted that their systems have been affected. The Ukrainian Computer Emergency Response Team said Odessa Airport was also hit. Also, there are reports of Bad Rabbit attack in Germany, Turkey, Poland, Bulgaria and South Korea.
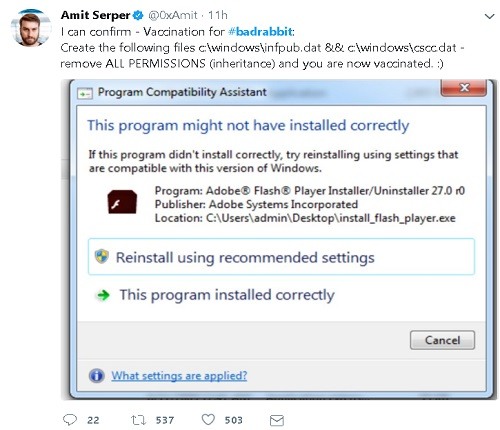
Security researcher Amit Serper tweeted a precautionary measure for Bad Rabbit which you can try out to ensure that you do not get affected.
Perpetrators of this attack have not been identified and no workaround has been found for infected computers. It is advisable not to pay any money to get data back as there’s no guarantee that the hacker will oblige; it also encourages them.
Source: Kaspersky, Securelist
Read our coverage of recent ransomware attacks here.






