Routing: How Do Packets Travel And What Happens Inside a Router?
If we talk about the computer networks, then it is incomplete without Routing. It is often…
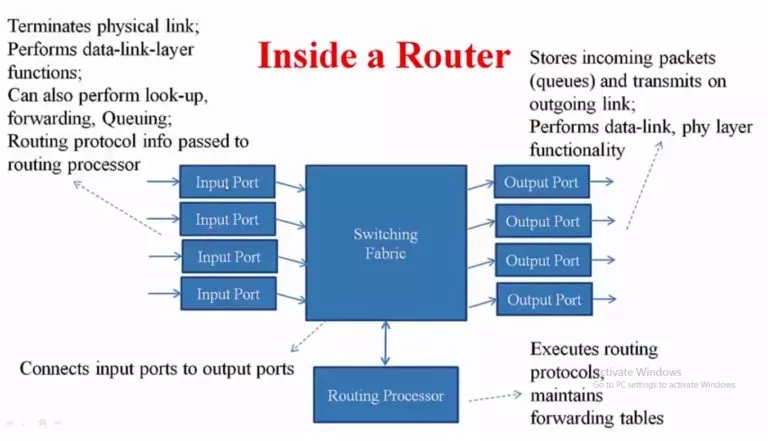
If we talk about the computer networks, then it is incomplete without Routing. It is often…
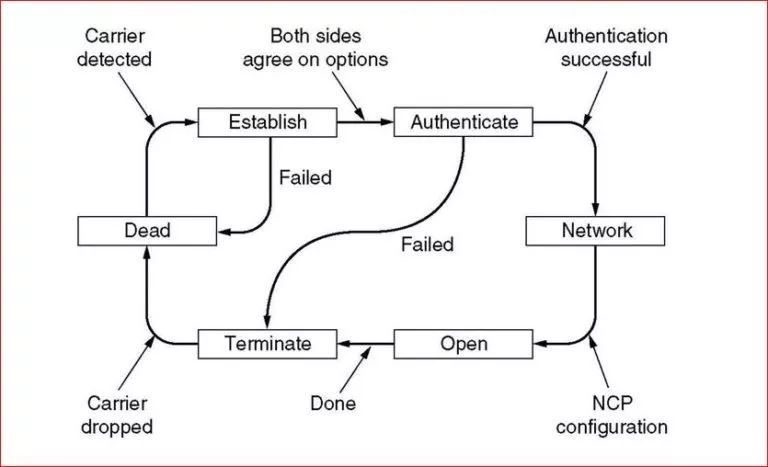
Often termed as “PPP,” point to point protocol is a data link layer protocol which is…

TM, also known as Asynchronous Transfer Mode, is a telecommunication concept, developed for the data link layer,…
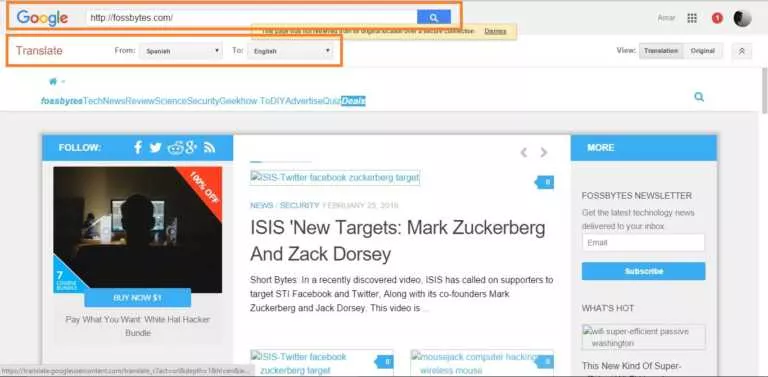
Short Bytes: There are different ways to use many services from Google as proxy servers to…
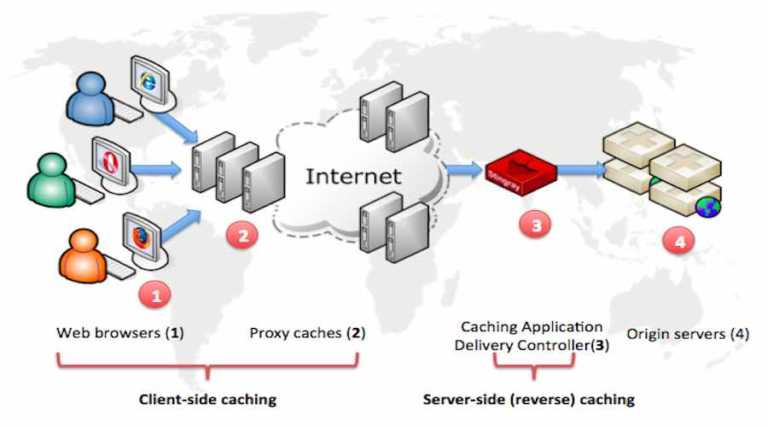
Short Bytes: Web caching is a network technology to deliver content faster to the web page…
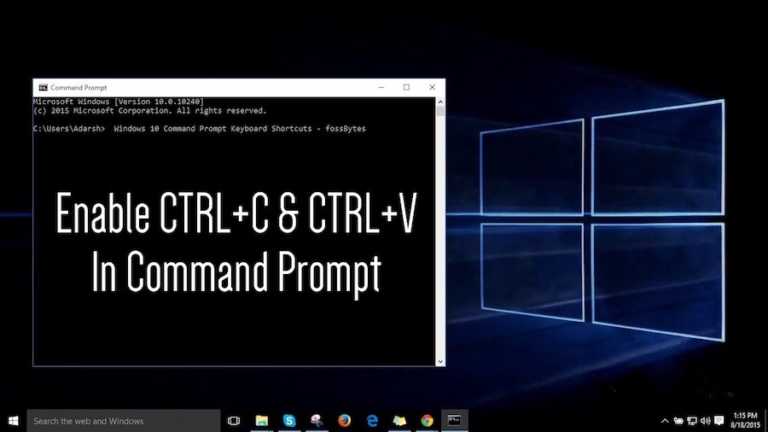
The copy-paste feature using the Ctrl+C/ Ctrl+V commands is one of the most used features of a…

Short Bytes: Firewall packet filtering rules are applied based on the integrity of the networks. There are three…

Short Bytes: Application layer attacks are the most favored ways of launching an attack. It just…

Short Bytes: The world’s fastest and stretchable IC has been created by a group of researchers at…

Short Bytes: To meet its upcoming projected production of the electric cars, Tesla is going to…