Android 9 Pie Safe From The WiFi Bug That Leaks Sensitive Data
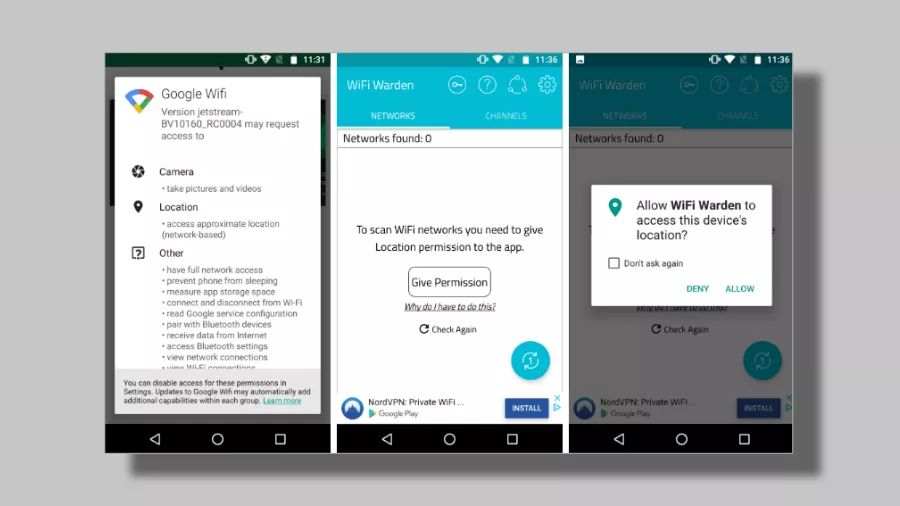
Researchers have discovered a vulnerability in all Android versions except Android 9, which could allow attackers to capture WiFi broadcast data and even pinpoint geolocation of users — all of this without user’s consent.
Nightwatch Cybersecurity posted a security advisory about the bug CVE-2018-9489, which states how the broadcasted information for installed Android apps can cause the device to be tracked easily.
Essentially, Android operating system uses a mechanism called “Intents” to send out information between processes or applications. And a broadcast using an “Intent” allows an application to send a system-wide message which can be listened to by other applications.
“While functionality exists to restrict who is allowed to read such messages, application developers often neglect to implement these restrictions properly or mask sensitive data,” mentions the advisory.
The system broadcast information that can be used for ill-intent includes the WiFi network name, BSSID, local IP addresses, DNS server information and the MAC address.
While the latter one is hidden via API from Android 6 and requires extra permission, an application listening to broadcast doesn’t demand any permission, thus capturing the information without the user’s knowledge.
The post also mentions that the MAC address can be used to “uniquely identify and track any Android device.” Furthermore, the SSID and network name can be used to geolocate users and even attack the local WiFi network.
According to NightWatch, Google spokesperson said the bug is fixed in Android Pie. But the company will not do the same for previous versions, leaving Android Oreo and other open to hacks and threats.
Also Read: How These Android smartphones Can Be Hacked With Simple AT commands