Hacker Tells How He Could’ve Hacked Tons Of Facebook Accounts Easily
 Short Bytes: A white hat hacker from California has shown how easily he could’ve exploited Facebook’s password reset mechanism to hack numerous Facebook accounts. He even hacked the account of a random Facebook user by collecting 2 million valid Facebook IDs and requesting their password reset codes in a short period of time. Then, he picked a random code and brute-forced all accounts in his database.
Short Bytes: A white hat hacker from California has shown how easily he could’ve exploited Facebook’s password reset mechanism to hack numerous Facebook accounts. He even hacked the account of a random Facebook user by collecting 2 million valid Facebook IDs and requesting their password reset codes in a short period of time. Then, he picked a random code and brute-forced all accounts in his database.
Once such account was recently published by security researcher Gurkirat Singh. In a blog post, he wrote about a security loophole in Facebook’s password reset mechanism that could have given him a complete access to the target’s Facebook account. By doing so, he could’ve viewed many users’ all private messages, view card details, or anything else.
Facebook’s password reset bug — Explained
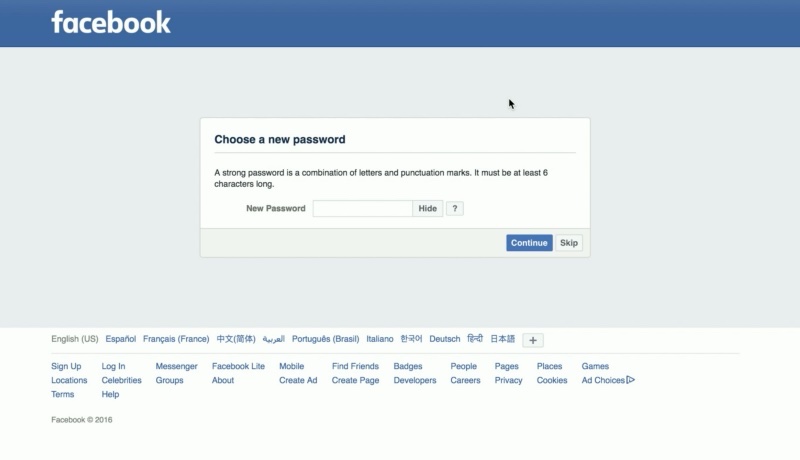
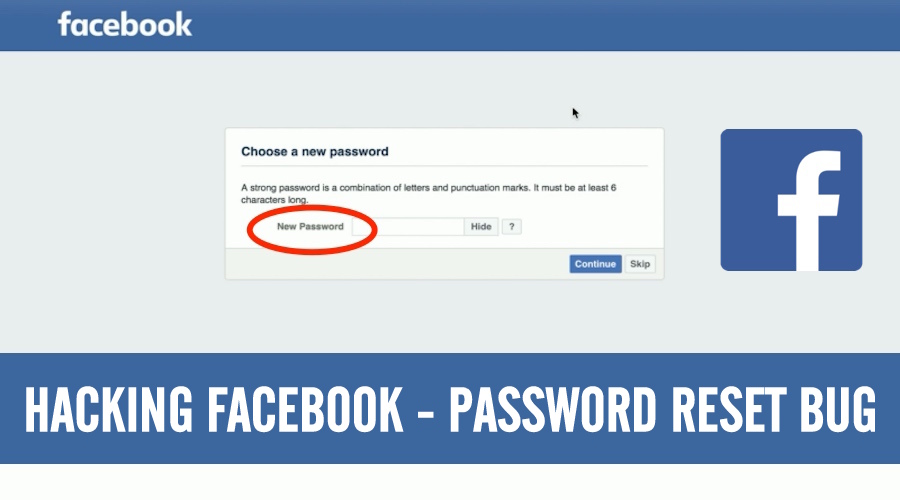
Explaining the bug, he tells how Facebook allows you to reset your Facebook password. The social networking website makes use of an algorithm to generate a random 6-digit passcode i.e. 10⁶ = 1,000,000 possible combinations. Interestingly, this code doesn’t change (if requested from mbasic.facebook.com) until it gets used.
So, if 1 million people request a password reset within a short period of time and no one uses the reset code, then 1,00,0001th person to request code will get a previously assigned number.
How to hack Facebook accounts by exploiting password reset bug?
To hack Facebook accounts and prove his point, Gurkirat collected 2 million valid Facebook IDs. He did so by making queries to Facebook’s Graph API starting with 100,000,000,000,000. This way, he easily got profile picture and full name of 2 million users.
Then, Gurkirat used a script to initiate the password reset request for those 2 million users. This process consumed the complete 6-digit range. In order to avoid getting his IP blocked from repeatedly sending password reset requests, he used a proxy server that assigned random IP addresses to each HTTP request.
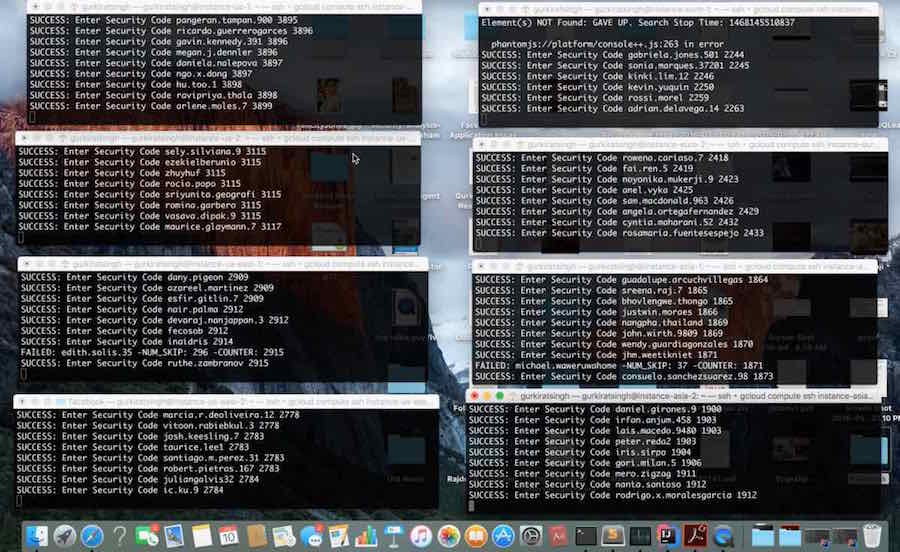
Here’s the huge amount of preparation done by him to run his script:
The next step involved picking up a random 6 digit password and brute forcing all the users in list database. In his words — “And guess what? I was able to find a matching ID.” Thus, he was able to get the complete access to a random user’s Facebook account.
Facebook has patched this bug after Gurkirat’s report and award him just $500 bounty. Gurkirat writes that despite being a critical bug, Facebook labeled his finding as low priority.
Here’s what Gurkirat has to say:
Important: Please note that this article is only for educational purposes.
You can read Gurkirat’s complete account here.
Did you find this article interesting? Don’t forget to drop your feedback in the comments section below.
Also Read: Story of Chris Putnam: The First Facebook Hacker