Rewritten GandCrab Ransomware Targets SMB Vulnerabilities To Attack Faster

GandCrab ransomware, which has created a hullabaloo in the cybersecurity industry by constantly evolving, has yet again caused a commotion. The latest version of the ransomware attacks system using SMB exploit spreader via compromised websites. The ransomware is adding new features every day to target different countries.
The attackers behind the ransomware are scanning the whole internet to find the vulnerable websites to unleash the attack. The latest version features a long hard-coded list of websites that were compromised and were used to connect with it.
A pseudo-random algorithm has been used by the attacker to select a predefined word to complete the URL for each host, and the final URL is generated in “www.{host}.com/data/tmp/sokakeme.jpg” format.
According to several reports, this newest version of the ransom can spread itself via an “SMB exploit.” Interestingly, the same exploit was used to propagate WannaCry and Petya/NotPeta ransomware attacks last year.
To propagate via SMB exploits, entire code of the ransomware was rewritten, and the malware is now using EternalBlue National Security Agency (NSA) exploits to attack in a fast-paced manner.
An investigation report suggests that a module going by the name “network f**ker” is accountable for SMB exploits.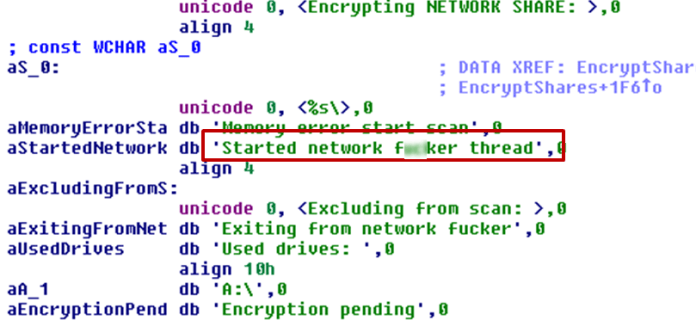 Fortinet, a cybersecurity company, said, “with GandCrab’s rapid development over the past week, and the public speculation of this exploit propagation functionality, we would not be a surprise if the threat actors decided to add it in a future update.”
Fortinet, a cybersecurity company, said, “with GandCrab’s rapid development over the past week, and the public speculation of this exploit propagation functionality, we would not be a surprise if the threat actors decided to add it in a future update.”
However, Microsoft has pulled up its guard against the ransomware with MS17-010 security patch. To protect your system, ensure that the system is updated with the latest security patch.
Also Read: 10 Best Free Antivirus Software For 2018 To Protect Your PC






