VPNFilter Router Malware Is Still Alive: More Devices Infected, New Capabilities Added
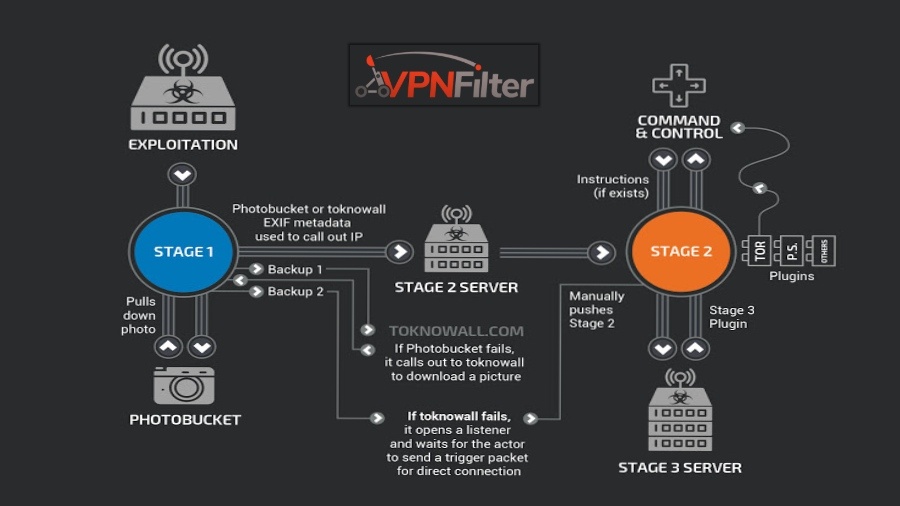
In late May, Cisco security researchers uncovered a router-hacking malware named VPNFilter, which was reported to infect more than 500,000 consumer Wi-Fi devices. At that time, the infected router belonged to companies like TP-Link, Linksys, MikroTik, and Linksys.
As per the latest development report, additional device vendors are being targeted by the malware. The new targets include ASUS, D-Link, Huawei, Ubiquiti, UPVEL, and ZTE. Notably, Cisco network devices remain unaffected, the researchers claim.
The additional discovery deals with a new stage 3 module that is being used for infecting web content as the traffic passes through a network device. It further grants a man-in-the-middle capability to the malware.
Called ssler and pronounded Esler, the module is aimed at fascilitating data exfiltration and JS injection via port 80. The researchers also expect it to be executed with a parameter list for deciding targets.
After infecting the router, first it configures the iptables to redirect all traffic to the local port and uses insmod command to insert various modules.
It further intercepts any outgoing web requests on port 80. The traffic can thus be inpected and manipulated before it reaches the HTTP service.
This development clearly shows that VPNFilter is continuously growing and its scope has expanded. It also means that VPNFilter remains alive even after you’ve followed FBI’s advice of rebooting the router.
You can read further details on the dangerous router malware in this Cisco post.
Also Read: How to Protect Your Wi-Fi Router From Hacking Using Simple Tricks