This Simple Hack Can Hijack More Than 1 Billion Android App Accounts

 Short Bytes: Three researchers from the Chinese University of Hong Kong have scanned multiple Google apps on the US and Chinese app store and found a serious vulnerability. This flaw resides in the way OAuth 2.0 is implemented in these apps. Due to faulty practices, a hacker can remotely exploit a victim’s app and access the personal information.
Short Bytes: Three researchers from the Chinese University of Hong Kong have scanned multiple Google apps on the US and Chinese app store and found a serious vulnerability. This flaw resides in the way OAuth 2.0 is implemented in these apps. Due to faulty practices, a hacker can remotely exploit a victim’s app and access the personal information.
Ronghai Yang, Wing Cheong Lau, and Tianyu Liu from the Chinese University of Hong Kong have looked at 600 most popular US and Chinese Android applications. Out of that, 182 applications, i.e., 41 percent of the total, supported single sign-on.
The researchers were able to spot issues pertaining to OAuth 2.0. For those who don’t know, it’s a standard that lets the users verify their logins on third-party apps using the Google or Facebook accounts.
What’s the issue with OAuth 2.0 that’s putting apps at risk?
Usually, when a user logs into any service using OAuth, the apps performs a complete check with the ID provider, like Google, Facebook etc. If the details match, OAuth gets an access token from the ID provider. This lets the app/service to allow the user to login using their Facebook or Google credentials.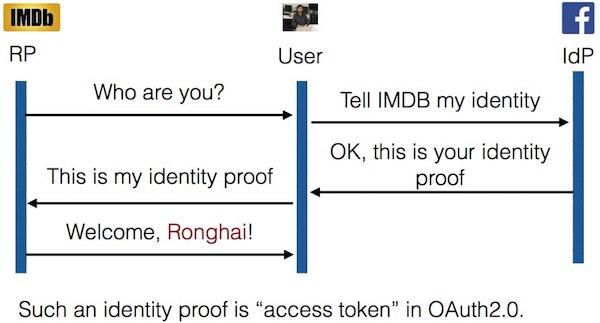
However, the researchers found that in a multitude of Android apps, the devs didn’t properly check the validity of the information sent by the ID provider. The mistakes included the failure to verify the signature attached to the authentication information retrieved from Google and Facebook, according to Forbes. Often, the app server would only check for the user ID retrieved from the ID provider. 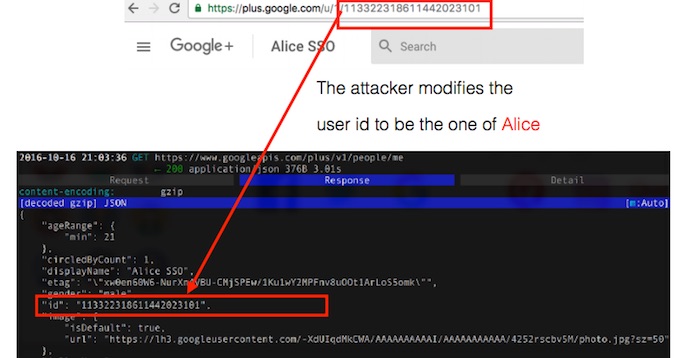
This could allow the hackers to download a vulnerable app and login with their own credentials and then switch the username of the target using a server that’s set to tamper with the data sent from the ID provider. This mischief would allow the hackers to get the total control of the data help within the app. The hackers can also remotely exploit an app to perform a sign in without victim’s knowledge.
Wing Cheong Lau, one of the researchers, said that even though the mistake is pretty basic, the impact could be severe. The OAuth protocol is quite complicated,” he told Forbes. “A lot of third party developers are ma and pa shops, they don’t have the capability. Most of the time they’re using Google and Facebook recommendations, but if they don’t do it correctly, their apps will be wide open.”
Did you find this article helpful? Don’t forget to drop your feedback in the comments section below.
Also read: Hackers Used Mirai Botnet To Shut Down The Internet Of An Entire Country